Get details on the most common toxic combinations Legit unearthed in enterprises' software factories.
Our "2025 State of Application Risk" report, which shares the results of our analysis of the Legit ASPM platform data over the past 18 months, provides insights into various aspects of application security, including secrets exposure, AI risks, SDLC misconfigurations, and software supply chain issues.
At the heart of this report lies the concept of "toxic combinations" in application security. Toxic combinations refer to the convergence of multiple risk factors that, when combined, create a significantly heightened security threat.
In the same way that driving at high speeds is risky, but driving at high speeds without wearing a seatbelt dramatically increases the risk of injury, certain combinations of security vulnerabilities can exponentially amplify the damage stemming from a cyberattack. For example, having exposed secrets in a repository with weak branch protection presents a much higher risk than either issue on its own.
Understanding individual risks
The analysis for the 2025 State of Application Risk report found that the below risks are some of the most common unearthed by the Legit ASPM platform in the past 18 months:
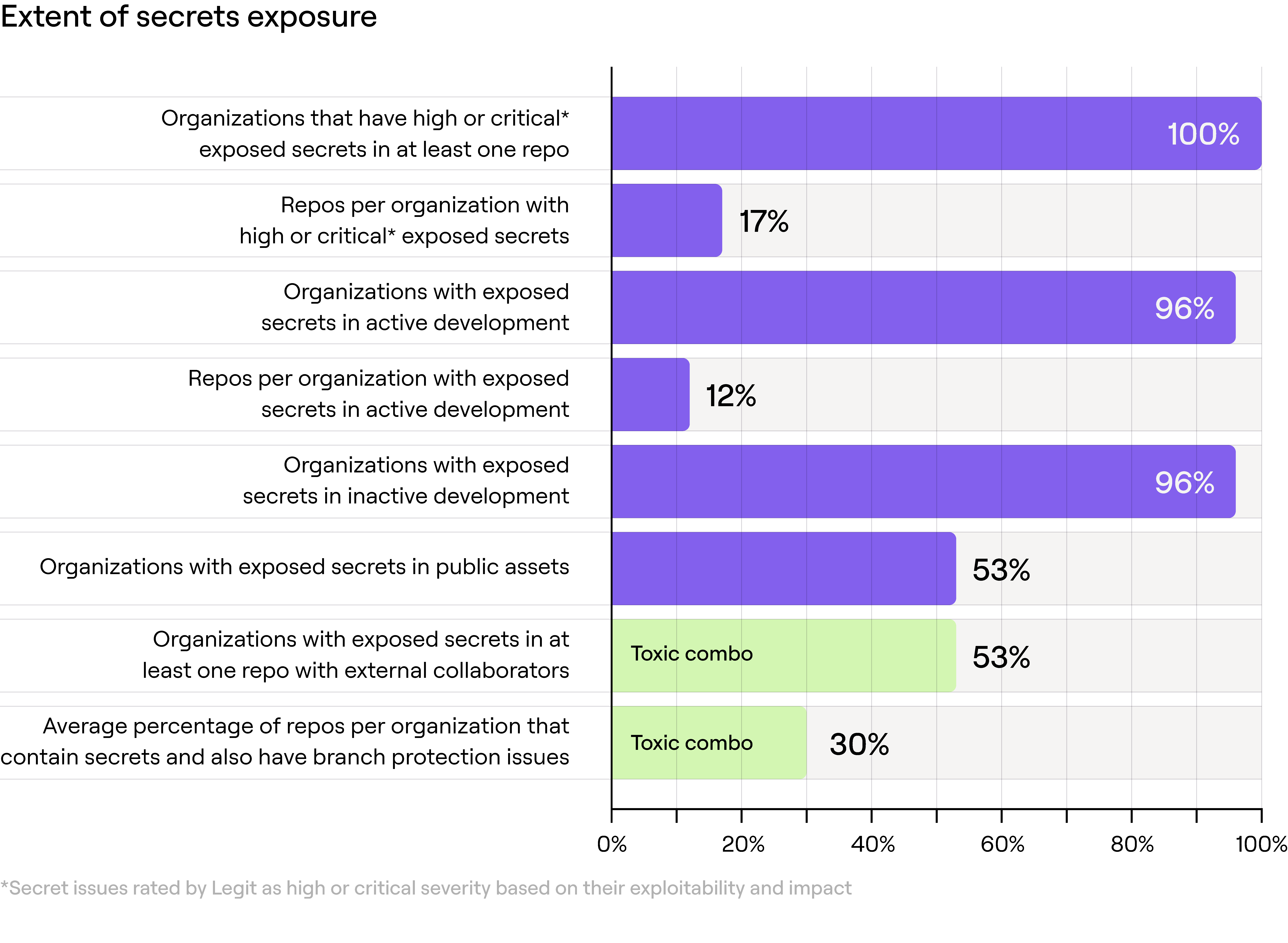
Secrets exposure: The report found that 100% of organizations have high or critical exposed secrets in at least one repository. Exposed secrets, such as cloud keys, personal access tokens, and PII, can provide attackers with an initial foothold for larger attacks.
External collaborators: These are developers who are not part of the organization, such as contractors. The presence of external collaborators can increase the risk of malicious activity in some cases, as demonstrated by incidents like the XZ backdoor attack.
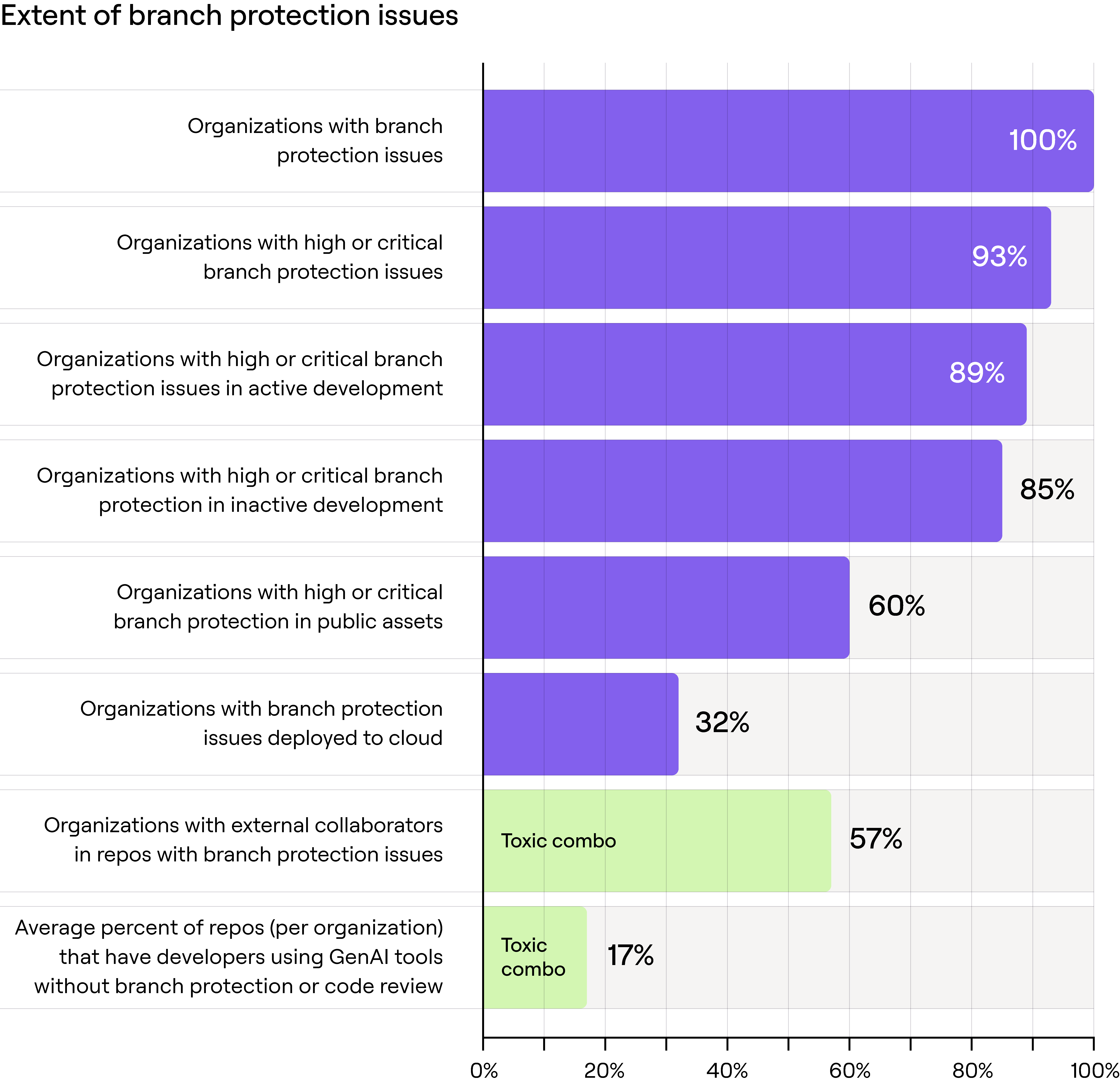
Branch protection: This feature restricts who can modify branches and how. Without proper branch protection, a single compromised account could allow an attacker to push malicious code directly to the main branch.
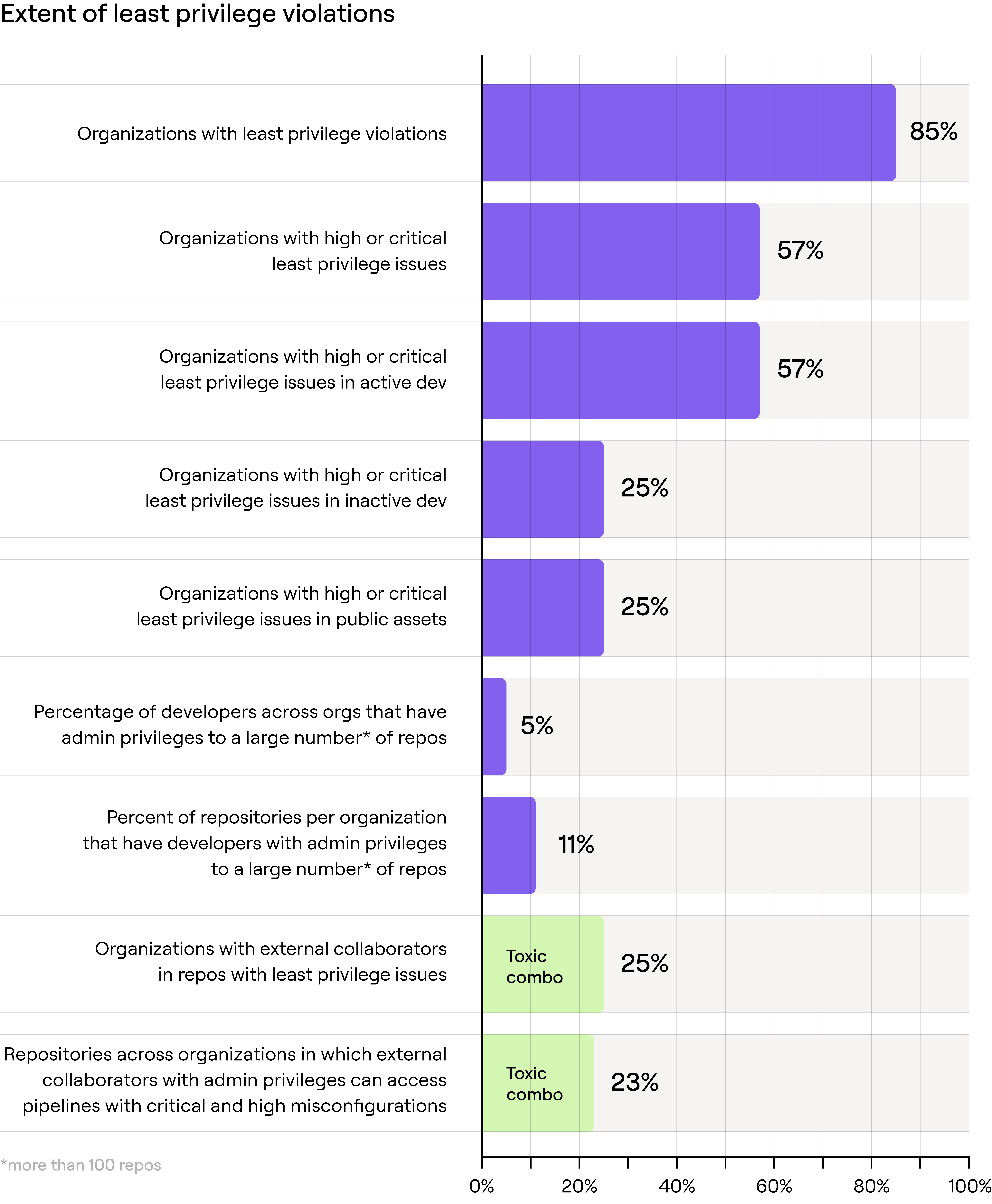
Least privilege: This principle involves granting developers only the minimum permissions necessary to perform their specific job functions. The report shows that 85% of organizations do not have least-privilege set up properly.
Understanding toxic combinations
When analyzing our platform data for the 2025 State of Application Risk report, we found that, in many cases, the risks above were amplified by combining with each other, or with other risks, forming toxic combinations.
Secrets exposure toxic combinations
The report reveals that 30% of repositories per organization contain both exposed secrets and branch protection issues. This toxic combination means that not only are secrets exposed, but the mechanisms to prevent unauthorized code changes are also compromised. An attacker who breached a system through exposed secrets would then have the ability to push code changes to the main branch.
Additionally, 53% of organizations have exposed secrets in at least one repository with external collaborators. This combination increases the risk of secrets being accessed and exploited by individuals outside the organization.
Branch protection toxic combinations
According to the report, 57% of organizations have external collaborators in repositories with branch protection issues. This toxic combination allows external parties to potentially make unauthorized changes to critical code.
Moreover, 17% of repositories per organization have developers using GenAI tools without branch protection or code review. This combination opens the door for AI-generated code to be integrated without proper scrutiny or safeguards, potentially introducing vulnerabilities or intellectual property issues.
Least privilege toxic combinations
The report found that 25% of organizations have external collaborators in repositories with least privilege issues. This combination gives outside parties potentially unnecessary access to sensitive areas of the codebase.
Perhaps most alarming, 23% of repositories across organizations allow external collaborators with admin privileges to access pipelines with critical and high misconfigurations. This toxic combination creates a perfect storm for potential security breaches, as it combines elevated access rights with vulnerable infrastructure.
Addressing toxic combinations
The 2025 State of Application Risk report highlights the critical need for a comprehensive approach to application security.
These toxic combinations underscore the complexity of modern application security. While individual vulnerabilities are concerning, their true danger often lies in how they interact with other weaknesses in the system.
A seemingly minor misconfiguration might not pose a significant threat on its own, but when combined with over-permissioned user accounts or exposed secrets, it could provide attackers with a clear path to sensitive data or systems.
Toxic combinations also highlight the need for solutions that go beyond identification of individual vulnerabilities to analyze the relationships between different types of risk. This approach allows security teams to prioritize their efforts on areas that pose the greatest threat.
Get more data and analysis on the toxic combinations unearthed by the Legit ASPM platform in the 2025 State of Application Risk report.
