Use the data and analysis in this report to prioritize your 2025 AppSec efforts.
We’re pleased to announce the publication of our 2025 State of Application Risk report. Based on anonymized data collected through our platform over the past 18 months, this report gives a clear picture of where application security risk lives in the modern development environment.
Further, it offers guidance on avoiding the type of risk in your development environment that leads to headline-making supply chain attacks.
Because our platform discovers and visualizes all aspects of both applications and the software factory producing these assets, plus all security controls and gaps, Legit is in a unique position to offer this detailed look at common areas of AppSec posture risk.
Application Risk Beyond Source Code
One thing made abundantly clear by recent breaches – and this research report – application security is no longer only about vulnerabilities in source code.
With software development that is faster, more automated, more dynamic, and highly reliant on third parties, new opportunities to introduce risk abound. From vulnerabilities in applications to misconfigured build servers, exposed secrets in Jira tickets, and more, the attack surface has grown and diversified.
And recent breaches, such as those at Codecov, LastPass, Sisense, and Kaseya, reflect the widening surface that attackers are targeting.
2025 Application Risk Highlights
Below we share highlights of the risks uncovered in this report.
AppSec testing inefficiencies
The extent of the risk we uncovered in this report results in part from an inefficient and ineffective process for assessing risk.
We found that a significant number of organizations have duplicate AppSec scanners producing duplicate results. As shown in the figure below, a whopping 78% have duplicate SCA scanners; 39% have duplicate SAST scanners.
When one scanner is telling the team that a finding is not worth remediating, and another scanner is giving them details on how to remediate it, confusion, and likely inaction, ensue.

Secrets exposure
Secrets are extremely pervasive in software development environments, and their exposure is one of the most common risks unearthed by the Legit platform.
Not surprisingly (but disconcerting), we found exposed secrets in 100% of organizations. The numbers drop to 53% for exposed secrets in public assets, and 35% for exposed secrets deployed to the cloud, but they’re still alarming numbers (see figure below).
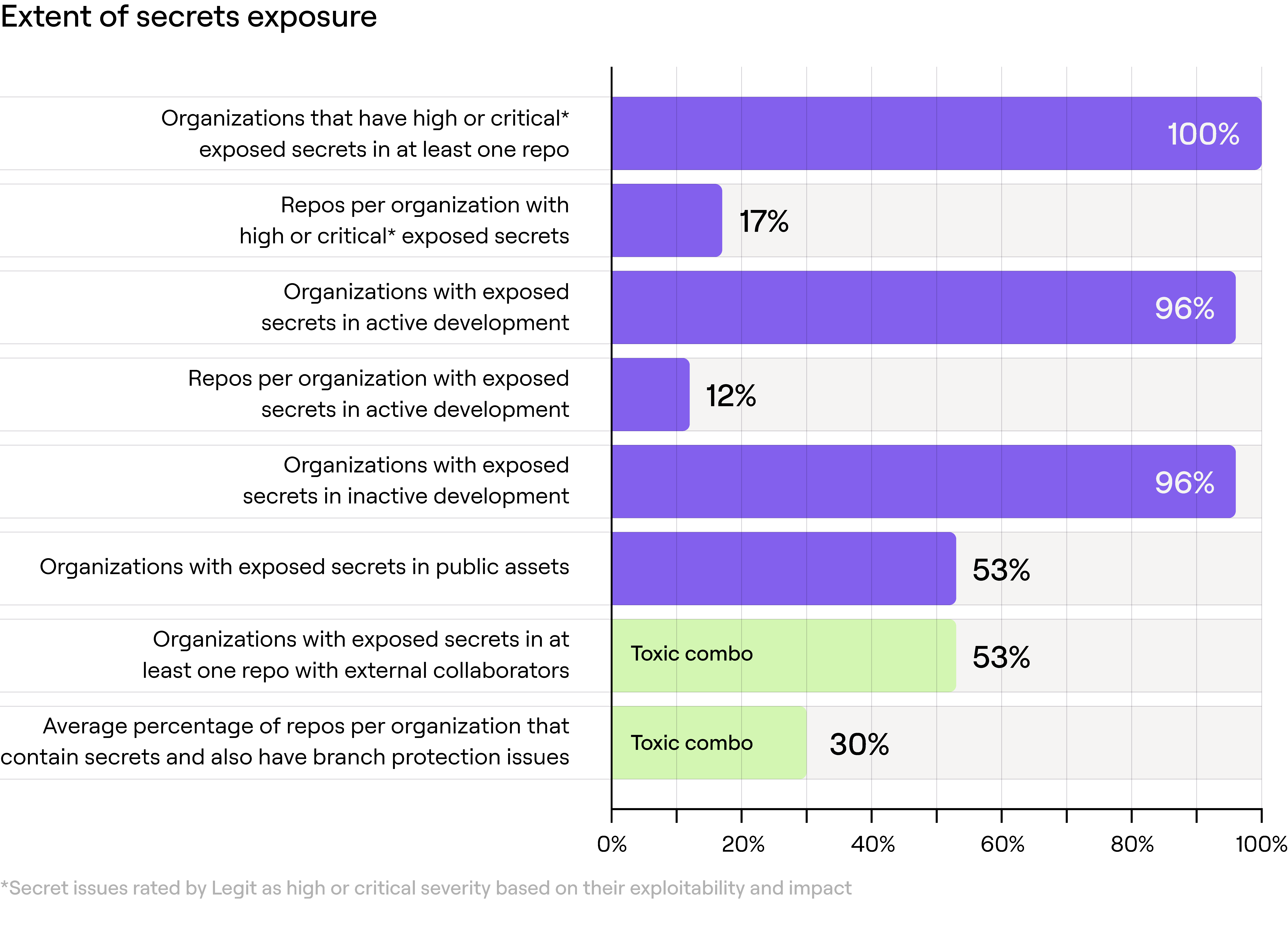
We regularly find exposed secrets in source code, which can be accessed by any user with access to the repository.
But increasingly, we are finding exposed secrets in many other places as well — like yaml files, build logs, containers, bash scripts, artifacts, containers, Jira, Confluence, Slack, and more. In fact, 36% of the secrets we found were outside source code.
GenAI risk
GenAI has recently emerged as an additional risk we uncover. Although it gives developers an easier way to produce code at scale, it also adds risk.
We often discover that security teams first don’t know where AI is in use, and then find out it’s used in a location that isn’t configured securely (see figure below). For instance, a developer is using AI and generating code on a repository that doesn’t have a code review step.
This could, for instance, allow for licensed code to enter the product, exposing the organization to legal or copyright issues.
We also often detect low-reputation LLMs in use, which could contain malicious code or payloads, or exfiltrate data sent to them.

Misconfigurations
A pipeline misconfiguration is one in a pipeline platform such as Jenkins, GitHub Actions, etc.
When we first start working with an enterprise, we often discover misconfigured build servers in their environment. This is a common problem, but also one that creates significant vulnerabilities.
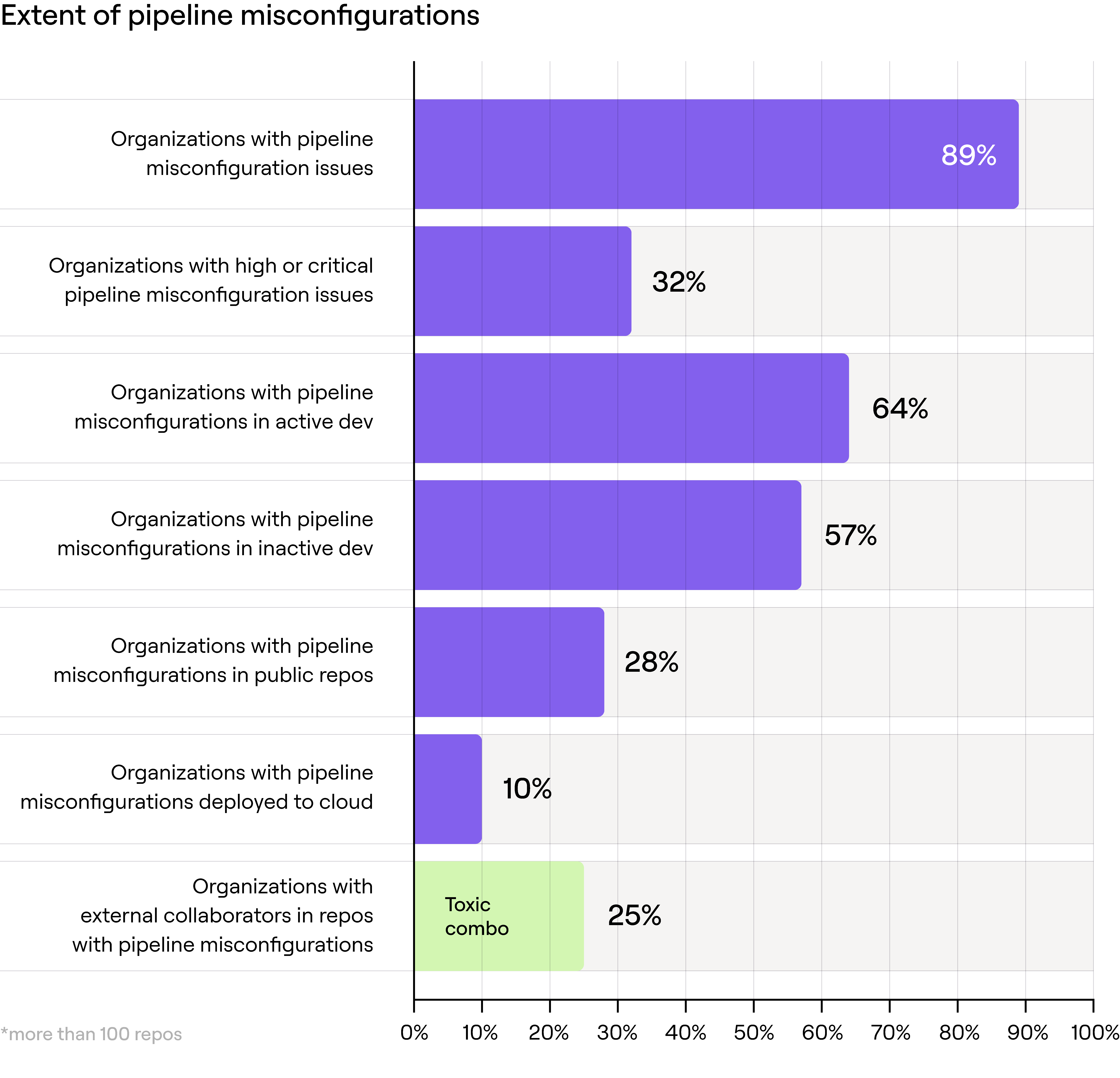
The figure below highlights our findings on pipeline misconfigurations. 89% had pipeline misconfiguration issues, with 64% of those in active development. Also noteworthy that 25% have the toxic combination of external collaborators in repos with pipeline misconfigurations.
Permissions sprawl
Mishandled developer permissions is a pervasive issue. When we first start working with enterprises, we almost always find overly and/or incorrectly permissioned development teams.
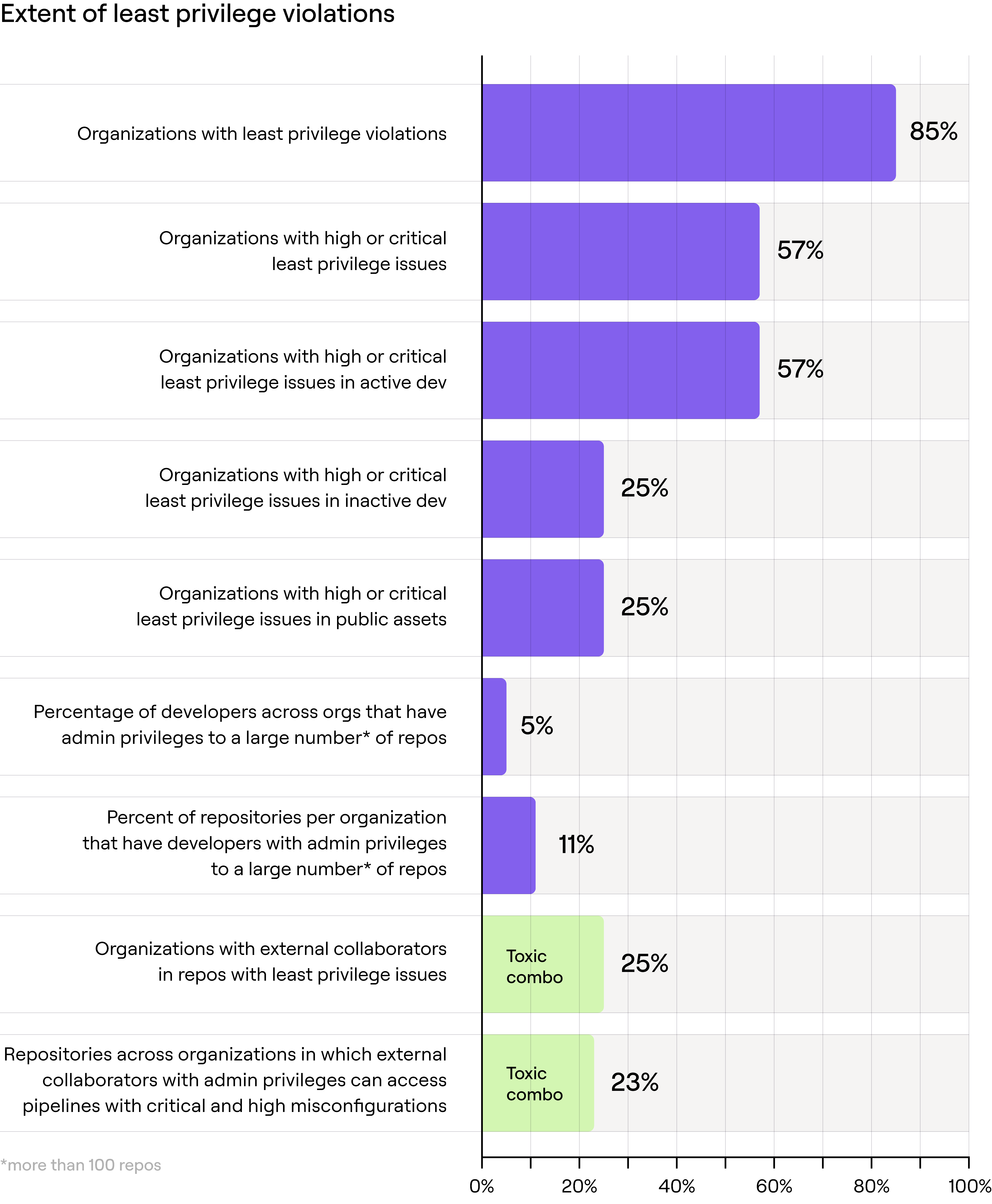
Our data shows that most organizations (85%) do not have least-privilege set up properly – meaning, developers have unnecessary access that would needlessly give an attacker extra access if those credentials are compromised.
On the good news front, the percentages are much lower for those with least-privilege issues in public assets (25%).
However, one-quarter have the toxic combination of external collaborators in a repo with least-privilege issues, and 23% have the toxic combination of external collaborators with admin privileges in pipelines with critical and high misconfigurations (see figure below).
Toxic combinations
A “toxic combination” refers to the ability to tie different types of risks together in a way that creates an attack path or an elevated combined risk.
We often find toxic combinations of risk when we first start working with an enterprise. Our ability to identify these areas of heightened risk helps teams prioritize where to start the remediation process.
Our analysis for this report revealed a number of prevalent toxic combinations, including the following:
- 53% of organizations have exposed secrets in at least one repo with external collaborators
- On average, 30% of repos per organization contain secrets and also have branch protection issues
- 25% of organizations have external collaborators in repos with pipeline misconfigurations
- 57% of organizations have external collaborators in repos with branch protection issues
- 35% of organizations have external collaborators in repos with software supply chain issues
Get all the data and analysis
Download The 2025 State of Application Risk report to understand:
- Where secrets are most often exposed, and how to reduce the risk
- The most common toxic combinations increasing enterprises’ application risk
- What types of SDLC misconfigurations are most common, which are the most risky, and how to avoid them
- The most common AppSec testing inefficiencies
- How GenAI is introducing risk in the development environment, and how to use it more securely
Start here to understand where the greatest application risks now lie, and to prioritize your own application security efforts.
Download our new whitepaper.


