Software Supply Chain Security
Automatically discover, analyze, and secure your end-to-end software supply chain.
Automated SDLC Discovery
In Minutes
- Discover and correlate your entire SDLC automatically
- Trace pipelines and dependencies from code to cloud
- Visual models of systems, pipelines and controls
- Expose and eliminate risky shadow IT environments
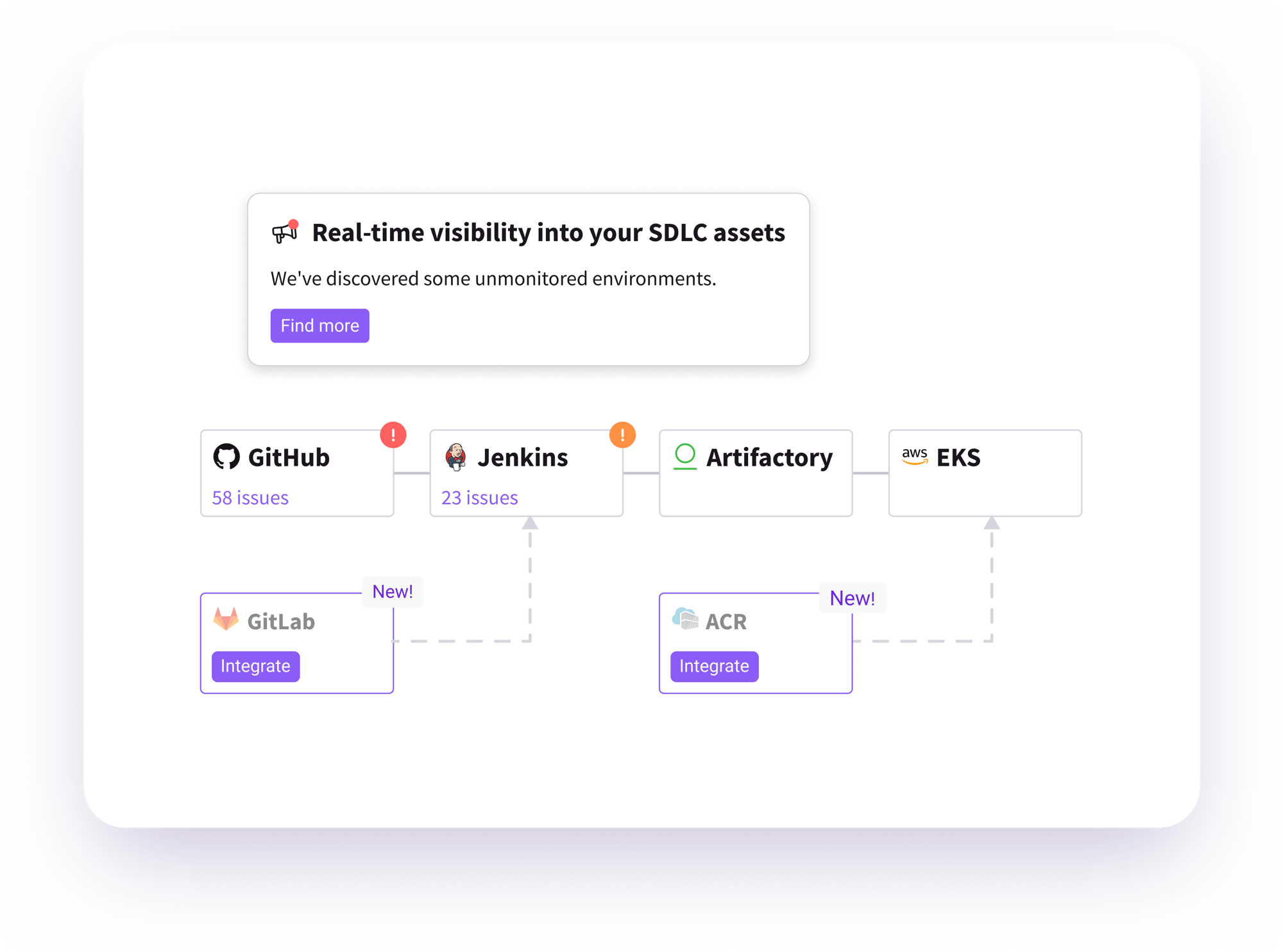
Real-Time Inventory Of SDLC Assets And Security Controls
- Continuously updated inventory of SDLC assets
- Identify security controls and close coverage gaps
- Ensure secure pipelines to the cloud
- Optimize security control placement, reduce redundancies and lower costs
Enforce Security, Resiliency And Software Integrity
- Enforce 100’s of policies to secure your software supply chain
- Secure SDLC systems, CI/CD pipelines, code and teams
- Ensure the integrity of every software release
Protect Sensitive Data In
Your SDLC
- Secret scanning and mitigation
- Prevent new secrets from entering the SDLC
- Prioritize secret remediation based on impact and relevance
Threat Hunting And
Custom Queries
- Investigate threats and risks with custom inquiries
- Perform rapid, ad hoc queries against your SDLC
- Save searches for ongoing use
Related Resources
-
 Read Nowanalyst reports
Read Nowanalyst reportsESG Survey: The Growing Complexity of Securing the Software Supply Chain eBook
TechTarget’s Enterprise Strategy Group recently surveyed 368 IT, cybersecurity, and application development professionals to understand current software development practices, the impact and challenges of software supply chain attacks, and how organizations are using software supply chain security solutions.
-
 Read Nowwhite papers
Read Nowwhite papersA New Approach to Application Security
Download the whitepaper and see how Legit is the new way to manage your application security posture for security, product and compliance teams.
-
 Read Nowwhite papers
Read Nowwhite papersThe Top Software Supply Chain Security Pitfalls and How to Avoid Them
Learn more about common supply chain security mistakes and how to avoid them.
See more
Related Posts
Request a Demo
Request a demo including the option to analyze your own software supply chain.
Request a Demo