As the modern DevOps revolution became prominent within most businesses, the SDLC security was typically an afterthought. Compounding that is the pervasive use of open source software, cloud-based services, etc. such that the software supply chain attack surface has a very wide and deep landscape. With the explosion of attacks in the modern DevOps stack, it has become a vital business requirement to provide security for software development.
The True Cost of a Security-Last Approach
A breach within the SDLC can provide hackers with the ability to traverse throughout the whole development stack and steal secrets, inject malware, infect the build, etc. The cost of these breaches could easily cost a company hundreds of millions of dollars, as seen in this IBM report, and potentially damage the company’s reputation/revenue/stock value/etc. to the point where they may even go out of business. Today’s security leaders understand the value, in terms of time and money, of shift-left with security solutions for their SDLC software development.
The hackers are going to look for the weakest link in the software development process. So, it is imperative that every phase of the SDLC be looked at and reviewed for secure software development best practices. For example, the comm100-installer hacker was able to access the build system CI/CD pipeline via a possible number of methods and create malicious binary distributions.
Tips for Securing Each Stage of the SDLC
This blog is focus on specific tips with respect to security software development lifecycle phases for developers and security leaders. It is not intended to be all encompassing since that would be very dependent on your application and development environments.
Securing the modern SDLC DevOps environments has see great progress in methods and solutions over the last couple of years. Today, most development teams use SCA and SAST tools that help with vulnerabilities within dependencies and coding methodologies. As hackers have shown, they are looking at the whole SDLC for the weakest area, which includes but not limited to; CI/CD pipelines, public facing &/or cloud assets, and shadow development systems.
Thus, today security professionals are now looking at the total SDLC process which includes securing/hardening development environments, software scanning technologies and process security controls/guardrails. On top of all this, is fully understanding the application development context to look for abnormalities, anomalies and other threat detection prevention. All this effort is to further shift-left the security focus and ultimately being pro-active vs re-active to securing the software development process. A more robust step-by-step guide for secure software development can be found here.
There are various SDLC Models with numerous phases, we’ll look at the following general SDLC phases:
- Planning
- Requirement – Gathering the scope of the feature(s) or product.
- Design – Technical design of the requirements.
- Development / Implementation – Writing the code that implements the design.
- Testing / Integration - Verifying that the functionality works as expected.
- Deployment and Maintenance – Releasing the functionality and continuously supporting it.
Planning
When planning for a new application build, the status-quo is not going to keep up with the security threats in today’s environment. Every application build should be continuously improving all aspects of the application, especially with respect to security. Developers and AppSec teams should be jointly responsible for the technology, people (training/skills) and process related to the SDLC security.
Tips
- Collaboration between Application Security Teams and Development Teams is critical for having a game plan for defining the SDLC security controls.
- See if a “gold” or “secure” application development pipeline/stack already exists within your organization. This will expedite the SDLC security controls/policies by providing a baseline to work with.
- Legit Security has a helpful list of other steps to follow when securing your software supply chain.
Requirements
Every organization should have standing requirements for the respective AppSec and Development team. If not, pick one of the Security frameworks (SLSA, SOC2, SSDF, NIST, ISO 270001) and get started. As you learn more, both from a framework and experience, you’ll fine-tune your related process, controls, and tools with every build. As referenced in the previous phase, identify a new security priority for each new application/build.
Tips
- What Governance/Frameworks does this application need to meet/exceed requirements?
- What Security Requirements / Policies (supporting Frameworks) does this Application require?
- What threats is this application going to be targeted?
- Incorporate industry-standard and/or frameworks security best practices.
- Assign accountability for software security. Best practice is to rotate through the Development and AppSec personnel to lead each new development.
- Follow our guide to a secure software development lifecycle.
Design
When you incorporate all the planning and requirements into the design, a secure SDLC checklist is helpful. This is most likely the last chance to continuously improve the SDLC process and security before writing any code. Understand the new security threats for your application so you can incorporate preventive measures as part of the design.
Regardless of architecture (IaC, VM images, Containers, etc.), work closely with your production support/security teams to incorporate the runtime security measures. Again, security up-front in the design is critical for shift-left and to allow the developers to build/deploy with speed.
Tips
- Define your Security Policies for the Application in advance.
- What type of secrets should we be validating?
- Incorporate threat modeling.
- Always have a rollback, mitigation and incident plan included in the design.
- Run architecture risk analysis.
- Identify early-stage vulnerabilities & remediate.
Development / Implementation
Putting it all together for secure software development. Leverage pipeline automations to continuously improve the application build process. Reference the secure SDLC checklist created previously to verify all requirements and process improvements are addressed.
Tips
- Use secure coding guidelines, SCA/Secret Scanners, for software development.
- Don’t forget the developer’s desktop and prevent Secrets from ever getting into your Source Code Management (SCM) systems.
- Leverage Secrete CLI scanners to look for secrets in directories/files and local Git repositories.
- Build your DevOps pipelines with the security controls/guardrails required.
- Include Secret scanner jobs for build files and build logs.
- Protect parameters/certificates in secret management solutions (i.e., key vaults).
- Leverage SBOMs for dependency vulnerabilities, compliance, etc.
- Avoid having “development dependencies," especially ones with known vulnerabilities, best practice is to use production dependencies for all software development stages.
- Manually review and peer review code to catch anything automated tools may have missed.
Testing/Integration
Expand your tooling for best practices in security testing for software development; SAST/DAST, API, etc. scanners. This phase is often the hardest since there are unlimited possibilities for testing parameters/options/configurations/etc. Continuous improvement is always an ongoing challenge, which can also be supported to adhering to an application security risk assessment checklist.
Tips
- Use multiple security testing techniques to cover all grounds.
- Penetration/Fuzz Testing SDLC threat modeling unit tests.
- IAST (SAST + DAST), API and other respective tooling.
- Review containers/configs and SBOMs as you prepare to deploy.
- Build an "always-on" approach to testing.
- Avoid having “development dependencies” especially ones with known vulnerabilities, best practice is to use production dependencies for all software development stages.
Deployment and Maintenance
Once an application has been deployed, the attack vector increases exponentially. Security tooling for production applications is vital. If application issues do arise, have incident plans in place for bugs, issues and quick software development and security.
Tips
- Monitor application performance and logs for any variations.
- Establish a schedule for patching/systems maintenance shutdowns.
- If downtime is not an option, use modern containers for continuous release versions.
- Use production automated security tools for continuous security monitoring and scanning.
- Have Code to Cloud traceability for instant visibility and quicker resolution.
- Always perform post-deployment team sessions to identify things done right and more importantly, lessons learn and how to continuously improve the SDLC security.
Keep Your Business Safe by Securing Your SDLC
As you are well aware, today's attack vector requires a secure SDLC. Most businesses have started this journey and unfortunately, there is no end in sight. As the modern software development process continuously changes (for the better) it requires a fluid, ever-changing security landscape for SDLC security controls and secure software development best practices.
A final tip, you can’t secure what you can’t see, so find a solution that starts with discovering the SDLC assets and their relationships, even shadow development systems.
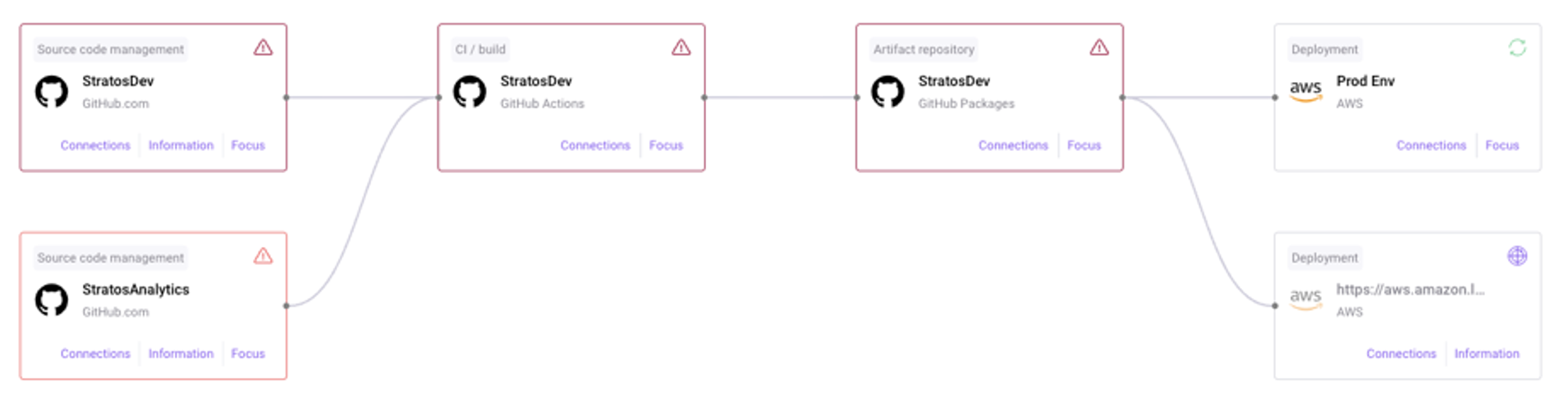
Needless to say, it only takes one compromised account or rogue system containing secrets, keys and other company sensitive data that could be the source for an attack, so please take the time to continuously improve, you’ll be happy (and more secure) that you did.
These insights should help you jumpstart securing your SDLC. Legit Security has a great resource library with Blogs, Videos, Guides, Best Practices and Webinars for additional reading. To learn more, schedule a product demo and check out the Legit Security Platform.
