On the 29th of September, it was revealed that the installer for the widely used Comm100 Live Chat application included malicious trojan malware. The installer was compromised using a supply chain attack on the Comm100 development pipeline. This attack was discovered by CrowdStrike and implied that state-sponsored hackers (allegedly China) backed organization was behind this attack.
Comm100 is a provider of customer services and communication products. The company says it serves over 15,000 customers in 51 countries. According to Reuters, “there are a dozen known victims, although the actual figure could be much higher.“
Customers that have downloaded the malicious trojanized installer are affected by this attack. The report states that this malware can steal sensitive data and information.
This attack was discovered only after the software supply chain of Comm100 was compromised. The effect of this kind of attack is crucial and should have been prevented beforehand rather than detected after the fact. In this blog post, we will show how this attack took place and how having a secure, solid software supply chain can help your organization from being compromised.
How Can I Tell If I Was Attacked?
According to CrowdStrike's report, the malicious installer was uploaded to the Comm100 servers on September 26, 2022. If you downloaded a version of this installer between the 26-29 of Sep, you should update your installer version ASAP.
Malicious Installer SHA256 -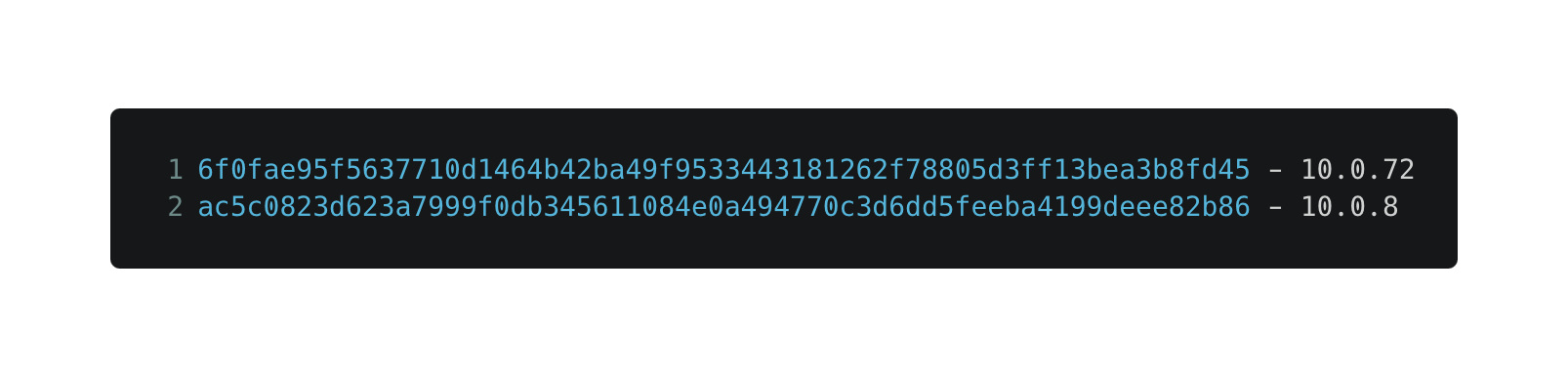
How did this attack happen?
The Comm100 installer was replaced with a trojanized installer which had the ability to steal information and sabotage compromised organizations. The malware was an Electron application that contacted a malicious server to collect information about the victim and create a remote shell session. The third part of the attack is downloading a malicious windows executable to gain persistence on the victim’s operating system.
The report does not specify this attack's origins but only shows the final critical outcome. We analyzed the attack and evaluated how this type of incident can happen.
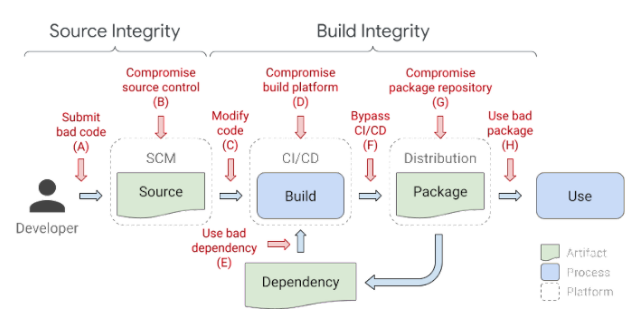
The software supply chain has many weak spots, and attacks like the Comm100 can happen in almost any of those.
Here is what we know:
The malicious installer was signed using Comm100’s code-signing certificate
This indicates that the software supply chain's vulnerable part was before the final code signing step. There are several ways this attack could have taken place:
-
It is most likely that the build system itself was compromised. This breach allows hackers to modify the build process and change the software’s delivery chain output, similar to what happened to SolarWinds in its 2020 attack.
-
Another option is that the malicious backdoor was pushed via a compromised developer account. This attack can happen if the attackers hacked a privileged user who can push code directly to the main branch without a proper default branch protection mechanism.
-
The third option for this type of attack is through a vulnerable SDLC asset, e.g., the SCM, the build system, its 3rd-party plugins, etc. A software organization must continuously update its SDLC assets. Recently, CISA added the Atlassian Bitbucket Server flaw to its Known Exploited Vulnerabilities Catalog, another example of how attackers can easily breach an organization with an outdated CI/CD environment.
There were two known malicious versions distributed
Two malicious versions were published, with a different minor version, showing that the attackers had persistence across Comm100’s CI/CD pipeline and could stay undetected until CrowdStrike could capture cases “in the wild.” It’s crucial to monitor and observe your CI/CD environment continuously so attacks like these won’t happen on your watch.
The attack group has previously targeted chat applications to distribute malware
Hackers are identifying the “blind spot” of many organizations. The software supply chain is not monitored, maintained, and developed as well as other areas in software companies.
As mentioned in the report: “The trojanized file was identified at organizations in the industrial, healthcare, technology, manufacturing, insurance and telecommunications sectors in North America and Europe.” This shows how attacking industry key-points can have devastating consequences even if the breach is alive for a short period of time.
How to prevent your CI/CD pipelines from being compromised
Software companies and organizations might pay a heavy price for letting their guards down. That’s why it’s essential to follow extra security measures to stay protected and keep your organization safe and sound. There are several steps you can take now to upgrade your CI/CD pipeline’s security:
Keep your secrets safe
Many times attacks such like this start due to leaked credentials. Always make sure your code doesn’t expose secrets to your CI/CD services. Employ guardrails throughout your development pipeline to provide continuous assurance.
Keep your SDLC assets monitored and updated at all time
You need complete visibility over your pipeline to ensure you know current versions and known attacks. This includes updating plugins or revoking parts of your pipeline that are not maintained.
Make sure developers' privileges are limited
Separating dev and prod environments, preventing access to secrets, and restricting pushing to default branches can assure that your organization will suffer minimal impact if one of your developer's accounts gets compromised.
Prevent artifact poisoning attacks
As we have previously shown, there are extra steps you can take to make sure “what you write is what you publish.” This will help detect changes in areas which are usually left un-watched.
Legit Security Prevents Software Supply Chain Attacks
The Legit Security platform automatically inventories your development environments and the relationship between systems. This encompasses source code management systems, build servers and artifact registries – all the way up until production deployment. Our SaaS platform alerts you in real-time when 100s of security policies are violated in your software supply chain so that security teams can remediate critical security issues before they make it into production.
To learn more, schedule a product demo and check out the Legit Security Platform.
-1.jpg)