Legit Security vs
Cycode Comparison
Compare Legit Security vs. Cycode in a detailed side-by-side analysis and discover why Legit Security stands out as the top ASPM solution for safeguarding your business.

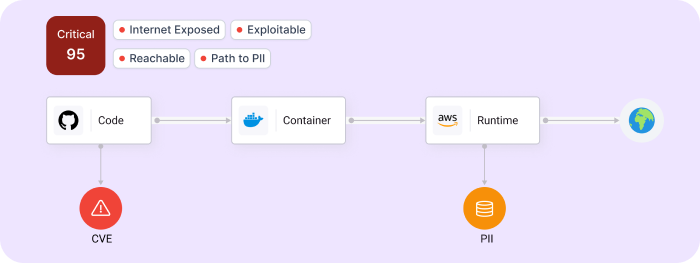
Context
Cycode uses change impact analysis or CIA to create material change logs and help build context within issue risk profiles. Legit also utilizes deep code analysis to build application inventory and understand material change, but in addition, it adds in additional context from analysis of pipelines and the creation of an SDLC inventory or pipeline BOM.
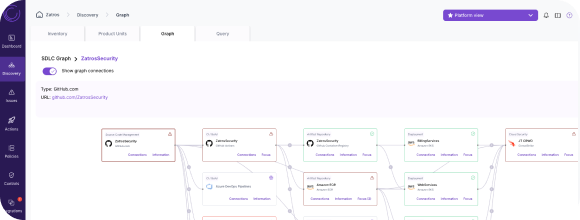
SDLC visualization
Legit offers discovery and a visual graph of SDLC build assets for complete visibility into the pipeline and code to production path, Cycode does not.
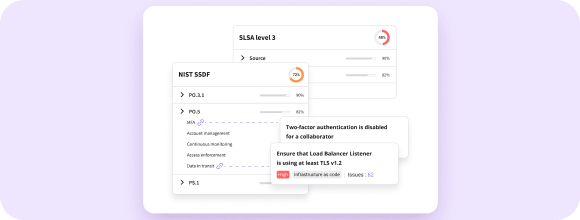
Framework mapping
Cycode does not map controls to compliance frameworks, whereas Legit aligns with multiple industry standards such as PCI-DSS, ISO 27001, NIST 800.53, SSDF, CISA Attestation, FedRAMP, SLSA, and OWASP standards.

AI inventory and posture management
Legit inventories and identifies risk in GenAI, LLMs and MLops usage; Cycode does not. As developers harness the power of AI and large language models (LLMs) to develop and deploy capabilities more quickly, new risks arise, including vulnerabilities, copyright restrictions, and data exposure. Legit helps security teams understand when and where AI is used in development and that it is being used securely.
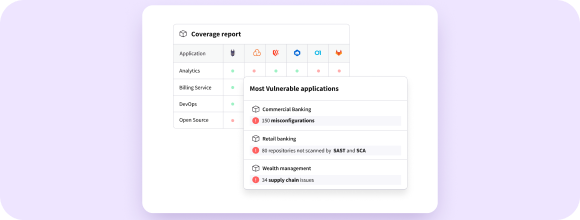
Integrating with scanners vs. built-in scanners
Cycode provides its own SCA and SAST scanners; while Legit offers these as well, along with its own IaC and pipeline scanners, plus integrations with premier AppSec scanners.
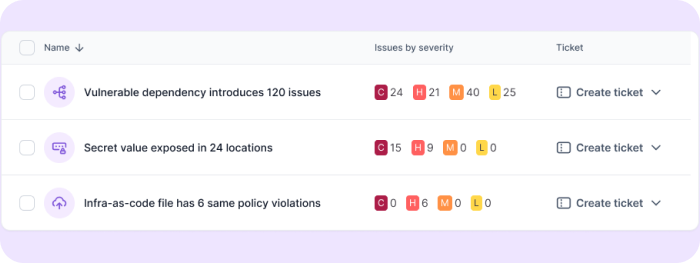
Remediation of risk
Cycode can help you prioritize your risk findings, while Legit helps you prioritize and address them with root cause remediation.
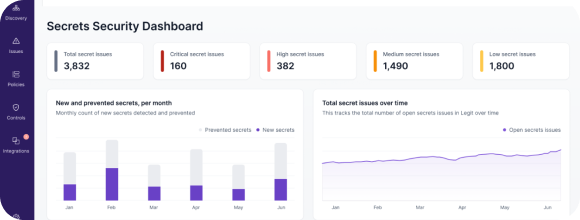
AI-powered false positive reduction for secrets
Unlike Cycode, Legit leverages AI to significantly reduce false positives in secrets detection. Legit has created a machine learning model that can process large volumes of code and be fine-tuned to recognize the nuances of secrets and when they should be classified as false positives. By understanding the context in which a secret is introduced, the model can accurately determine whether it should be flagged. This approach minimizes false positives while maintaining stable true positive rates.
The solution also features “Active Secret Validation,” which attempts to confirm the validity of a secret, further increasing the certainty in our predictions.
When Legit applied its AI/ML to over 10,000 manually labeled samples from open-source projects, they reduced false positives by 92% with negligible impact on true positives, meaning significant noise reduction and improved risk prioritization.
Why is Legit Security the Best Alternative to Cycode?
The following are just some of the capabilities that set Legit Security apart from competitors.
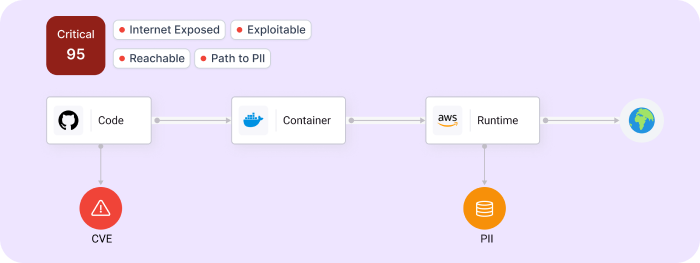
Legit context
Legit context provides enterprises with a clear view of their true risk posture and key remediation priorities by unifying various data points, including an application's business criticality, Internet exposure, sensitive data handling, API exposure, and AI usage.
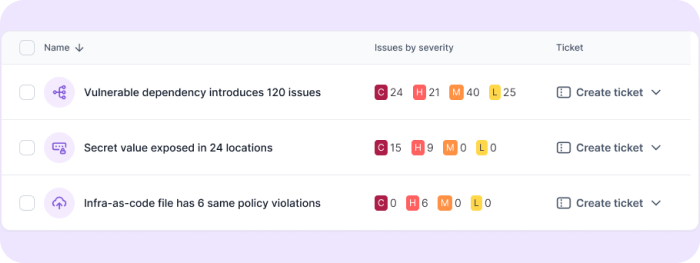
Legit root cause fixes
Legit is now the only ASPM platform to support root cause remediation actions, empowering organizations to reduce AppSec risk by fixing issues at the true source of the problem. By pinpointing the choke points where remediation actions can address multiple issues at once, security teams accelerate risk reduction and reduce the burden on developers.
Speed to operationalize
Customers quickly have the Legit ASPM platform up and running and highlighting their development environment and its security controls.
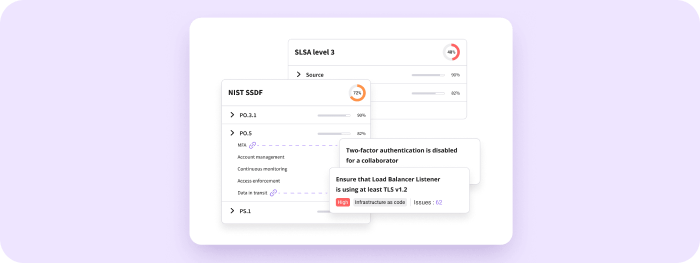
Compliance framework mapping
Legit maps your security guardrails to regulations, including PCI-DSS, FedRamp, NIST 800.53, SSDF, CISA Attestation, SLSA, and OWASP. With real-time monitoring and alerts on compliance violations, Legit eases the burden of complying with regulations.
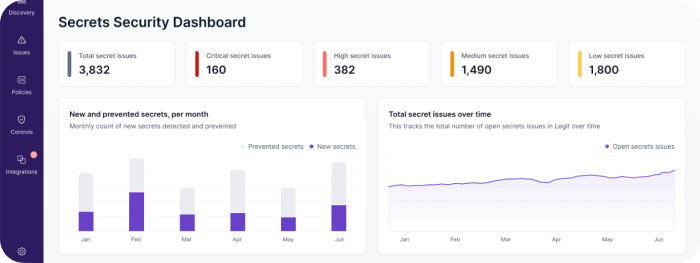
AI-powered false positive reduction for secrets
Legit, unlike Cycode, utilizes AI to drastically reduce false positives in secrets detection.

AI inventory and posture management
Legit inventories and identifies risk in GenAI, LLMs and MLops usage; whereas Cycode does not.
Request a Demo
Request a demo including the option to analyze your own software supply chain.
Frequently Asked Questions
Legit helps teams:
• Gain a complete and unified view of application risk
• Use deep context to prioritize and take action
• Proactively fix existing and prevent future issues

Announcing the 2025 State of Application Risk report
Report | State of Application Risk
Gartner® Innovation Insight: Application Security Posture Management
Report | Gartner® Innovation Insight: Application Security Posture Management

Legit Platform Overview
A comprehensive platform to protect your most critical assets:applications and the software factories that produce them
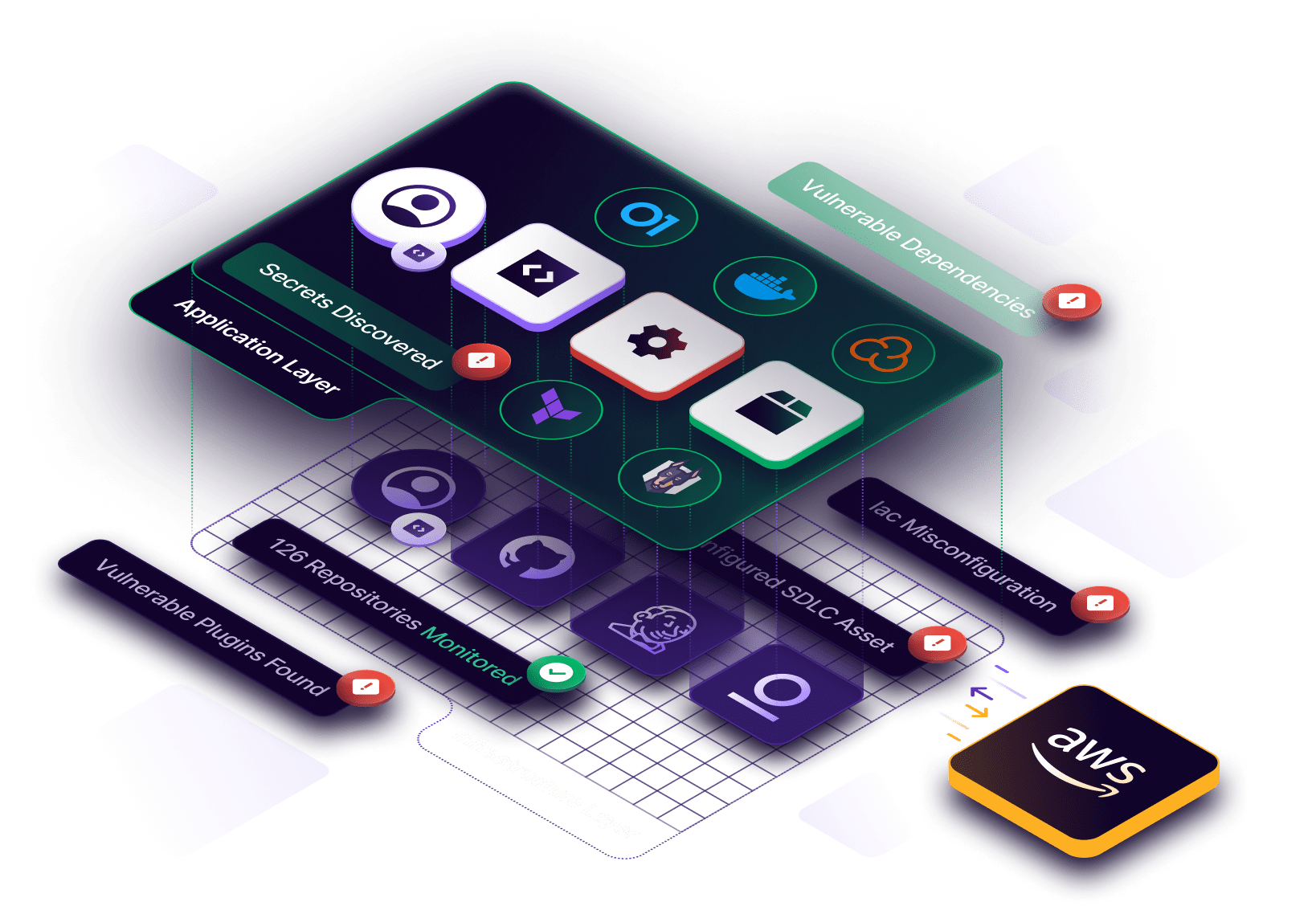
ASPM Platform
Legit is an ASPM platform that automates security issue discovery and prioritization. A trusted ASPM vendor option for your supply chain.
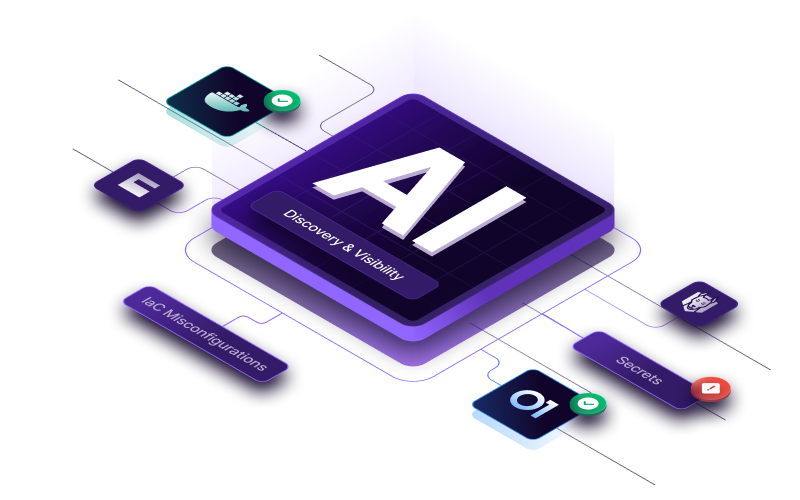
AI Discovery
Bridge the gap between security and dev by uncovering where and when AI code is used and take action to ensure proper security controls are in place - without slowing software delivery.
Announcing Legit Context: The Missing Link to True Business-Driven ASPM
Get details on Legit's new capabilities that allow AppSec teams to focus on the issues posing real risk.
Related Posts
-
 Read moreblogs
Read moreblogsWhat Is Application Security Posture Management (ASPM)?
Strengthen your business with application security posture management (ASPM). Plus, explore how Legit Security’s AI-native ASPM safeguards your organization.
-
 Read Nowblogs
Read NowblogsWhat Is AppSec? Application Security 101
Discover the fundamentals of what AppSec is, its importance, types of tools, and best practices to protect your applications from vulnerabilities.
-
 Read Nowblogs
Read NowblogsSecrets Scanning: How It Works and Why It’s Important
Discover how secrets scanning protects sensitive data beyond source code, including documentation, developer tools, and artifacts.
A Foundation You Can Trust
Get a stronger AppSec foundation you can trust and prove it’s doing the job right.
Request a Demo