Secrets Detection & Prevention
Modern secrets detection & prevention to identify, remediate, and prevent secrets – everywhere.
Tackle Secrets Sprawl Before Attackers Do
Secrets are vital to software development today; modern apps use hundreds of secrets to operate. API keys, access tokens, credentials, and other secrets ensure the security of applications and data, and enable non-human identities to communicate. And, secrets are everywhere, found far beyond source code. With such value comes risk – secrets are a prime target for attackers seeking to infiltrate your software supply chain.
Secrets are everywhere – far beyond source code
Secrets are continually added by developers
Secrets live in history and shadow assets forever
Secrets scanning is burdened with false positives
Legit’s Next-Gen Secrets Detection & Prevention
Uncover secrets creating risk
Legit uncovers secrets wherever they reside in your developer environment because source code is only the tip of the iceberg. From ticketing & ITSM systems, artifact registries and shared workspaces such as Confluence, Jira, and Slack, to your developers’ personal GitHub accounts, we go deep to identify every secret. We even unearth secrets hiding in Git history.
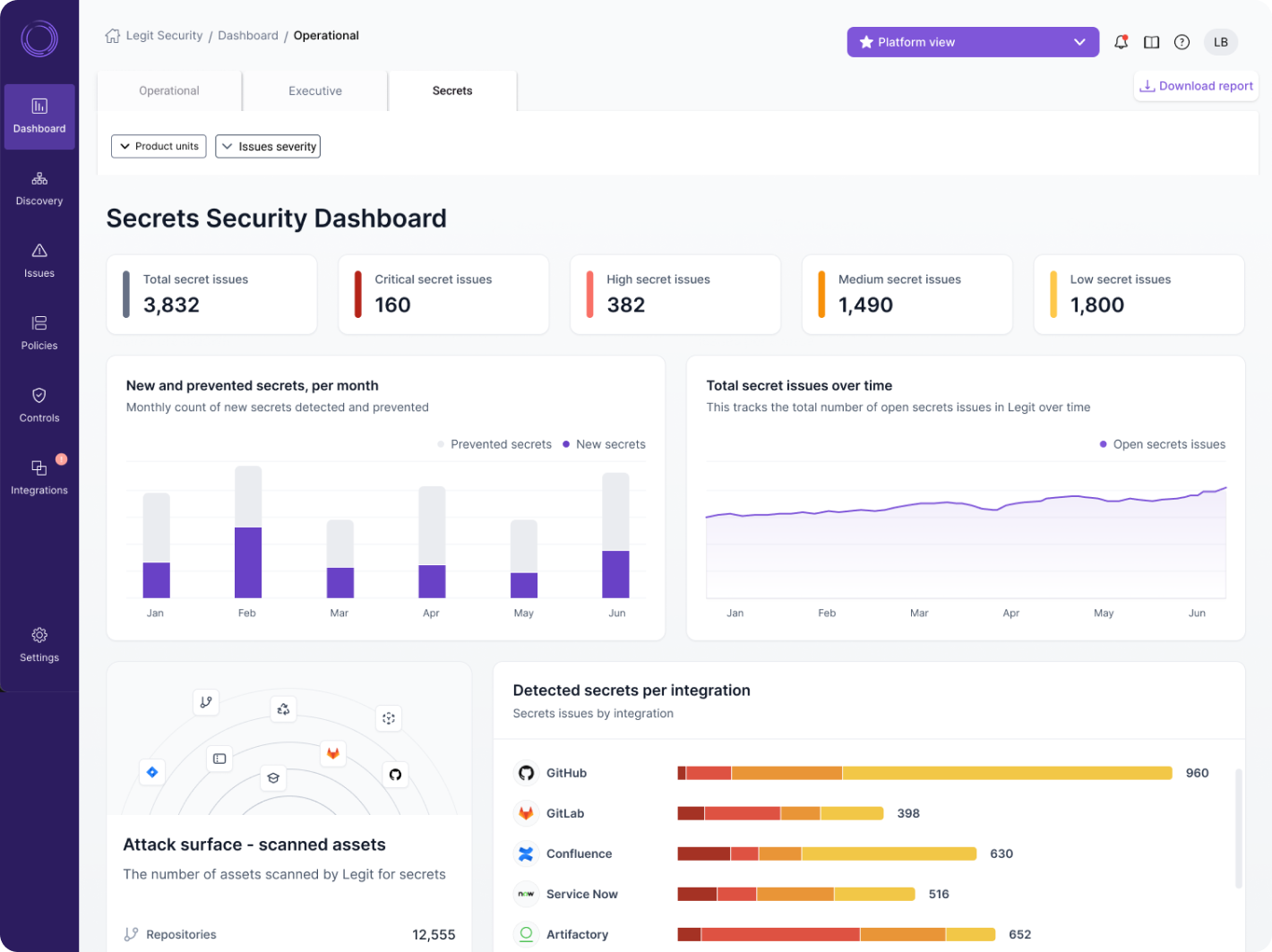
Analyze & visualize secrets
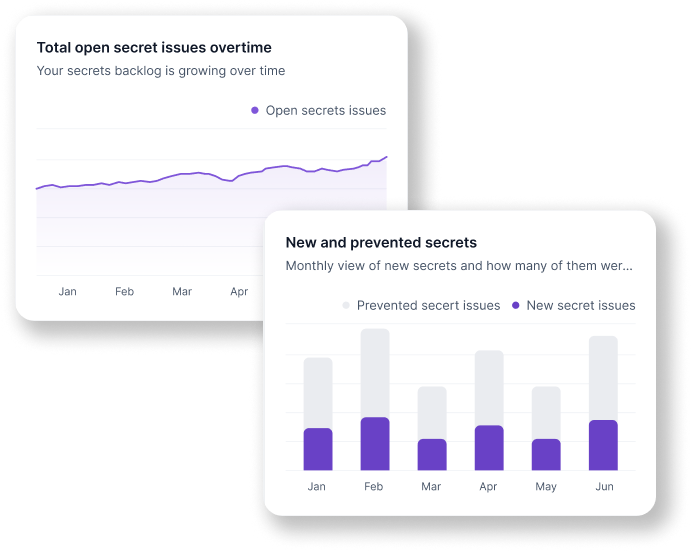
Legit analytics provide a deep view of secrets and the associated security activities. With our centralized dashboard, you have one view of all secrets detection and prevention across the enterprise. Your teams will benefit from a simple, clear way to gain a complete view of your secrets posture.
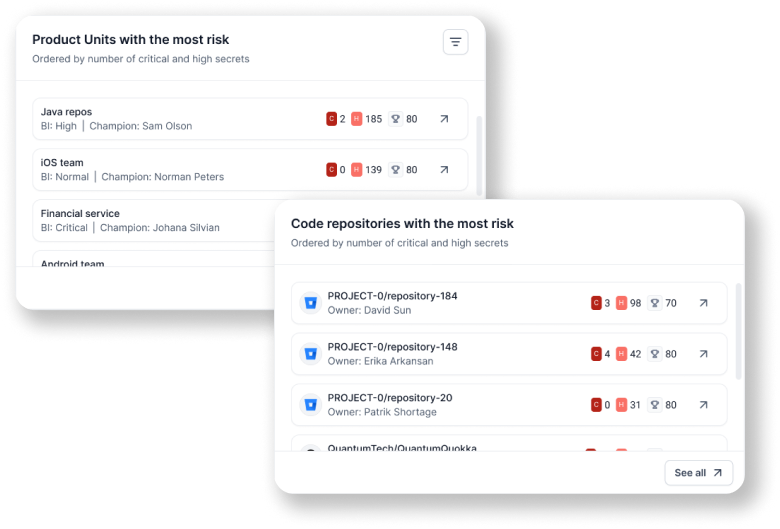
Remediate risk that matters
Legit helps you to prioritize developers’ work based on risk to the business. We dive deep into your secrets to prioritize remediation based on factors such as severity, source, repo, and user. Legit’s automation and orchestration capabilities enable you to immediately fix any existing secrets. Legit also provides a simple view of new secrets, plus remediation and backlog trends so you can assess the effectiveness of your AppSec program.
.png?width=521&height=395&name=Remediation%20(2).png)
Actively prevention with automated guardrails
Legit allows you to stop the bleeding with automated guardrails that can actively prevent new secrets from emtering the developer environment. This can be extended all the way to the individual developer endpoint with the Legit CLI.
.png?width=521&height=395&name=Prevention%20(2).png)
Get secrets scanning with AI-powered accuracy
Unlike open-source tools, Legit has a continually learning engine with a low rate of missed detections to find all secrets in your SDLC, while the platform delivers extensive context and prioritization capabilities to limit the impact of false positives.
CISOs
Secrets are a top area of risk to the business. Legit provides an executive-level view of your secrets posture so you can understand and communicate risk status and trends.
AppSec
Exposed secrets open up avenues to infiltrate your applications and software supply chain. Legit helps you identify and fix the issues that matter most.
Cloud Engineering
Secrets are the key to allowing cloud services to interact, communicate, and do their jobs. With Legit, you can protect these lifelines and ensure your services are secure and resilient.
Platform Engineering
Developers rely on secrets to build and deliver the apps your business relies on. With Legit, you can ensure the platform services that enable developers to do their job remain secure and protected.
Security Operations
Because secrets are so prevalent, they play a central role in expanding your overall attack surface. With Legit, you can reduce this risk by ensuring secrets are identified, remediated, and prevented.
Business Benefits of Secrets Detection & Prevention
Developers often use secrets in code, from passwords to PII that make development and testing easier and allow for faster innovation; however, poor management of these secrets can expose sensitive information publicly or to malicious actors.
Discover secrets beyond source code – in ticketing & ITSM systems, repos, artifact registries, and even developers’ personal GitHub accounts – to cover your entire dev environment.

Get to the root cause of existing and future secrets by tracking them back to the original source for quick resolution and preemptive training.

With Legit’s AI-powered detection, you’ll reduce false positives by nearly 90% - cutting wasteful alerts and reducing your mean-time-to-remediation.

Prevent secrets from creating future risk by implementing guardrails and policies that ensure developers can do their jobs – securely.

Legit AI-Powered Secrets Detection and Prevention
Experience first-hand the power of the preventative capabilities Legit enables with a 2-week free trial.
Start Your Free TrialRelated Resources
-
 Read Nowdatasheets
Read NowdatasheetsLegit Secrets and Detection Prevention
Get an overview of Legit's secrets scanning capabilities.
-
 Read Nowwhite papers
Read Nowwhite papersOvercoming the Challenge of Protecting Secrets in the SDLC
Find out how secrets end up in your code and how to protect them.
-
 Read Nowwhite papers
Read Nowwhite papersThe Top 6 Unknown SDLC Risks Legit Uncovers
Find out the top unknown SDLC risks we unearth, plus how to prevent them.
Request a Demo
Request a demo including the option to analyze your own software supply chain.
Request a Demo