On May 5th, Gartner published an Innovation Insights Report that outlines the latest evolution in AppSec– Application Security Posture Management (or ASPM for short). ASPM is something that we at Legit Security have been pioneering for over a year – a revolution in the way modern application security can be done more efficiently and effectively.
In this post we will provide more insights into the elements of ASPM so you can better understand how this new approach transforms traditional application security and enables organizations to deliver secure applications at scale.
Why ASPM? - Application Complexity and Organizational Security Siloes
Modern applications are complex. Multiple trends have culminated together to increase this complexity and the resulting challenges to securing applications. These include microservices and cloud-native architectures that make applications more modular and fragmented, use of 3rd party open-source software, automated CI/CD pipelines, cloud transformation and development teams that are remote and more distributed. All this creates many moving parts which require multiple security scanning tools and techniques that cross multiple teams: security, engineering, DevOps, CloudOps and more.
Each scanning technique is traditionally done individually, and by organizational group, and creates a silo. Organizations purchase many point scanners such as SCA, SAST, DAST, Infra-as-Code and more, each covering a fragment of the application and operated independently of the rest.
Traditional Application Security Shortcomings
Under modern application conditions, traditional AppSec fails, causing the following challenges:
- Too many noisy siloed products, all providing a piece of the security posture of the application, and inability to assess the unified application risk profile.
- Disconnect between different teams, which makes remediation efforts challenging.
- Contextless noise and duplications, creating extreme challenges to determine the root cause and owner of security issues, and to prioritize what to fix next.
- Missing visibility and governance, resulting in failures to cover all application components with their needed security controls.
- Operational challenges to configure and orchestrate scanners and security guardrails to achieve secure application delivery across the enterprise.
How ASPM Modernizes Application Security
To tackle all these challenges, a new unified and holistic approach is needed that can succeed where traditional AppSec fails. It is built on a foundation of unified visibility and governance from code to cloud, or from code creation, through development pipelines and processes, and into production environments.
The ASPM approach begins with strong visibility and context into the SDLC and into how applications are built and deployed. From the developer to source code repositories, build systems, artifact registries and runtime; including all components, pipelines, automations and security guardrails along the way. This provides traceability and deep context for all vulnerabilities and the basis for strong application governance.
An ASPM solution aggregates all risks across the pre-product development environment to provide a single view, which also analyzes trends, security coverage and provides contextual risk scoring to each application release.
Gartner created a graphic to represent core ASPM capabilities as shown below.
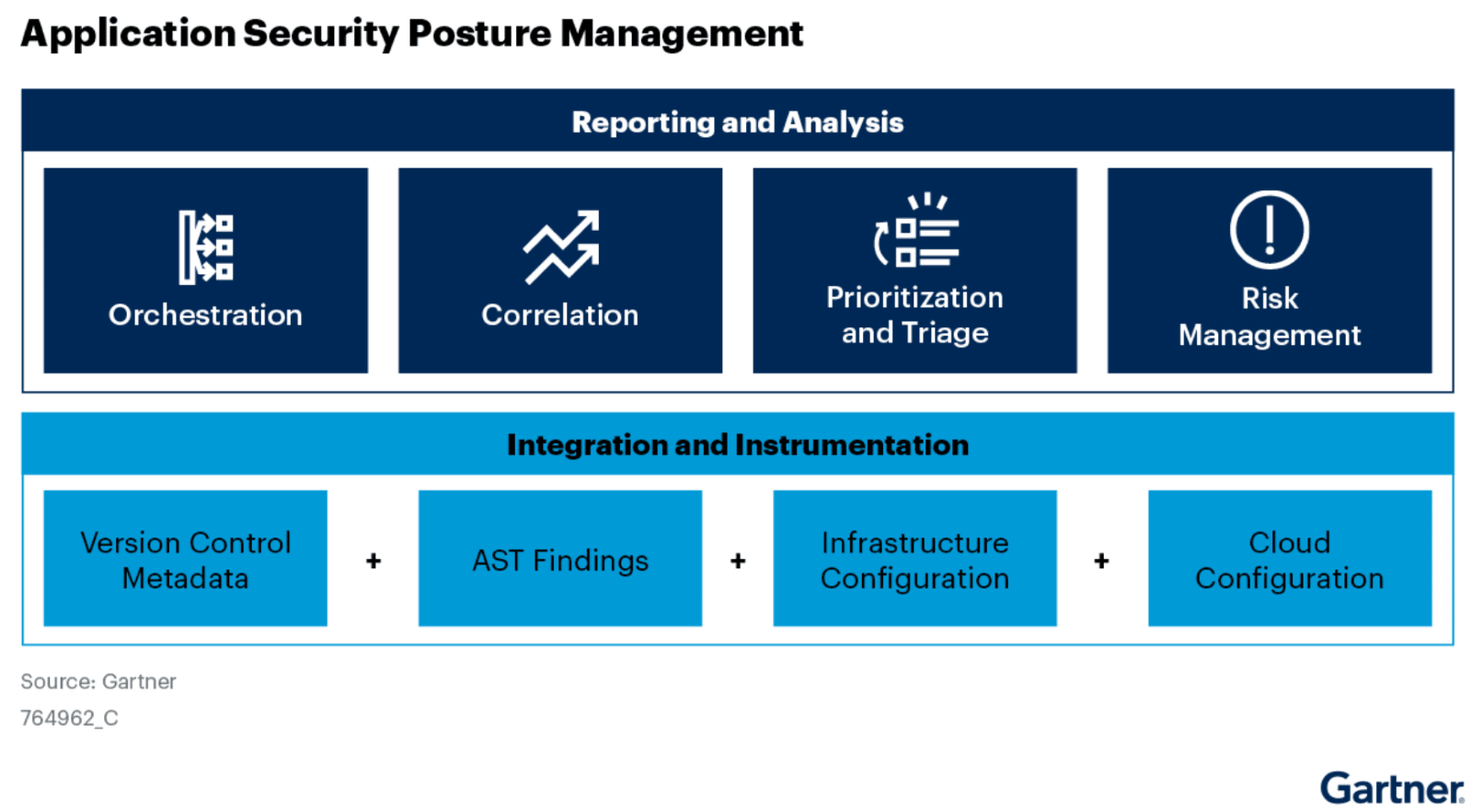
Gartner identifies 7 key core components of an ASPM solution as follows:
- Coverage: Includes all AST technologies and development infrastructure, from code to runtime. For example, an ASPM solution has to connect to the SCM (source code management system), other SDLC systems and infrastructure, and also to the runtime environment where the application that went through this pre-production development environment ultimately deployed.
- Testing orchestration: This includes the ability to integrate testing tools into the pipeline. For example, controlling which tests will be running as part of a pull-request check.
- Remediation: An ASPM solution needs to provide guidance on how to fix vulnerabilities and help establish remediation workflows by identifying ownership, enabling triage, integrating with ticketing and alerting systems and more.
- Correlation: A key ASPM capability, correlation refers to data grouping of similar characteristics to allow better prioritization and faster remediation. For instance – looking at all vulnerabilities originating from the same file, or relevant to the same container. In some cases, also merging duplicate findings that reference the same problem.
- Prioritization and triage: ASPMs provide data and context to make better decisions – which can be intelligent risk scoring, prioritization based on business context and application criticality, and more. Most development shops have huge risk backlogs and need to surface the most critical risks to fix at any given time with their limited resources and ASPM can help.
- Root cause identification: Providing the means to either manually or automatically identify root causes for risks by leveraging traceability. For example, it is possible to identify the file or component that is responsible for the most risk or point out to a project that adds significantly more vulnerabilities over time relative to others. This makes remediation efforts more efficient by addressing the risky sources and trends.
- Risk management: ASPM solutions can aggregate and report on the overall application risk, by means of scoring, calculating business risk and impact, and more. This allows an organization to make better decisions, set goals and track progress over time.
ASPMs can add value in two other very important areas:
- Software supply chain security – ASPMs can protect the SDLC itself in addition to the application builds that flow through it. Software supply chain attacks have increased between 3-6X annually in recent years, and protecting this attack surface has become an essential security need. This includes the need to secure CI/CD pipelines, SDLC systems and infrastructure, generate SBOMs and verify application integrity.
- Application security testing out-of-the-box – ASPM solutions can also provide their own native security scanning capabilities, such as secret scanning and IaC scanning. An ASPM should provide orchestration capabilities to the security scanners that come with the solution, in addition to connecting to pre-existing 3rd party vendors.
ASPM Benefits and Business Value
- Better coverage and enforcement of security controls – ASPM’s visibility and governance capabilities can help determine which aspects of an application are missing a security guardrail, and to build secure CI/CD pipelines that ensure that each change goes through the most secure process. Automating and enforcing security checks allows early, faster, and "closer-to-the-source" remediation which greatly increases efficiency and security.
- Focus on what’s most important – ASPM’s context gathering and correlation capabilities provide the means to automatically prioritize the most critical risks first. A holistic application definition makes it easier to more accurately calculate the business risk associated with a vulnerability. For instance, is it part of a business critical application deployed to external production or instead a less critical app for internal use?
- Contextual policies – ASPM context helps abolish the “one-size-fits-all" policy that is traditionally applied across applications. Context can not only drive remediation but also define a tailored policy for enforcement. A public open-source code project should have strict secret prevention, whereas for a private project some restrictive configurations can be relaxed.
- Collaborate and span across security silos – According to Gartner, using multiple security tools by multiple groups creates “silos of responsibility, visibility and control throughout the organization”. An ASPM approach allows all the teams to collaborate together, share a common risk view and security policies. This reduces friction and creates focus on the most relevant issues which ultimately reduces application risk.
- Faster, more streamlined remediation workflows – ASPM operational capabilities and integrations with ticketing and alerting systems combined with application intelligence make it simpler to create automated remediation workflows that reach the correct owner. This results in issues that get fixed faster and with less resources.
Legit Security – ASPM Pioneer and More
The Legit Security Platform has been designed with the ASPM approach in mind from the start, and focuses on visibility, discovery and traceability from code to cloud. Legit shows the overall application posture and helps prioritize and triage all risks. In addition to the core ASPM capabilities identified by Gartner, Legit also comes with a comprehensive software supply chain security solution, protecting the SDLC, sensitive development data, and driving secure development practices and hygiene.
Legit uses graph technology and a discovery and correlation engine to bring superior visibility and context into application risk and to allow all stakeholders to prioritize what’s relevant first. It’s architected as a unified platform that ensures secure application delivery end-to-end, all with an agentless approach that requires 5-minute API integration with the development systems that span the SDLC.
ASPM is Projected to Grow Fast
Gartner predicts growth from 5% to 40% adoption of ASPM within only 3 years. Like Gartner, we believe that ASPM is becoming essential to modern application security, especially for organizations with complex development environments, DevOps, CI/CD, distributed teams, and complex application portfolios.
The ASPM approach is here to stay. Legit Security, as an early pioneer and leader of this market, is determined to continue innovating so organizations can release their software more securely and more efficiently.
To learn more about ASPM, get the Gartner® Report: Hype Cycle™ for Application Security, 2023 or get a demo of our platform to learn about Legit Security’s approach to ASPM.
