On March 29th, 2023, it was published that 3CX, the international VoIP IPBX software, was under an ongoing software supply chain attack. The attackers had trojanized the 3CX communication installer software, reportedly used by over 12 million users daily. Several endpoint security vendors, such as SentinelOne and CrowdStrike, identified this attack. Some reports link this attack to the notorious Lazarus group, the cybercrime group linked to the government of North Korea, as part of their wide activity targeting software vendors to gain exponential impact.
The 3CX company, which develops the 3CXDesktopApp, an enterprise call routing software that enables voice and video conferencing using a Private Automatic Branch Exchange (PABX) system, asserts that it has over 600,000 customers and 12 million users across 190 countries. Among its clientele are renowned corporations such as Mercedes Benz, American Express, BMW, McDonald's, Ikea, Pepsi, and many more top-tier companies.
On April 20th, it was published by Mandient researchers' that the attackers gained access to the 3CX developers' network through a trojanized version of the X_TRADER software. X_TRADER, shipped by Trading Technologies, was also under a software supply chain attack carried out in early 2022. In Their report, Google's TAG showed how the Trading Technologies website was compromised using a phishing attack. Once they gained network access, attackers began moving latterly to gain control over the Windows and macOS build environment.
Customers that have downloaded the malicious installer are facing significant risk because the 3CX software is intended to handle internal communication and access sensitive information. The malicious program can also collect sensitive information stored on victims' computers.
Who is affected by this attack?
3CXDesktopApp users should verify their installed version. According to CrowdStrike, the malicious files were:
|
Filename |
Operating System |
SHA256 |
Installer SHA256 |
|
3cxdesktopapp-18.12.407.msi |
Windows |
dde03348075512796241389dfea5560c20a3d2a2eac95c894e7bbed5e85a0acc |
aa124a4b4df12b34e74ee7f6c683b2ebec4ce9a8edcf9be345823b4fdcf5d868 |
|
3cxdesktopapp-18.12.416.msi |
Windows |
fad482ded2e25ce9e1dd3d3ecc3227af714bdfbbde04347dbc1b21d6a3670405 |
59e1edf4d82fae4978e97512b0331b7eb21dd4b838b850ba46794d9c7a2c0983 |
|
3CXDesktopApp-18.11.1213.dmg |
macOS |
92005051ae314d61074ed94a52e76b1c3e21e7f0e8c1d1fdd497a006ce45fa61 |
5407cda7d3a75e7b1e030b1f33337a56f293578ffa8b3ae19c671051ed314290 |
|
3cxdesktopapp-latest.dmg |
macOS |
b86c695822013483fa4e2dfdf712c5ee777d7b99cbad8c2fa2274b133481eadb |
e6bbc33815b9f20b0cf832d7401dd893fbc467c800728b5891336706da0dbcec |
Users who still suspect their installer to be vulnerable can use different virus scans such as VirusTotal.
The story behind the attack
This attack is fairly new, and not all details are known at this point. We advise readers to stay tuned to this blog post for new information and updates.
The different reports do not specify this attack's origins but only show the final critical outcome. We analyzed the attack and evaluated how this type of incident can happen:
-
The malicious installer was signed using 3CX’S code-signing certificate.
The software supply chain was vulnerable before the final code signing step. This discovery suggests that the attack could have occurred through various means. The most probable scenario is that the build system itself was compromised, allowing hackers to alter the build process and modify the software's delivery chain output, similar to the 2020 SolarWinds attack. Another possibility is that the attackers exploited a weak link in the Software Development Life Cycle (SDLC), such as the Source Code Management (SCM) or third-party plugins used by the build system. It is essential for software organizations to regularly update their SDLC assets to prevent vulnerabilities from being exploited. -
Several vulnerable versions were distributed.
According to CrowdStrike, four malicious versions were published, showing that the attackers had persistence across 3CX’s CI/CD pipeline. Keeping a continuous eye on your CI/CD environment is critical to prevent similar attacks from happening under your watch. -
The distributed malware is complex and supports different operating systems.
Once installed, several steps are taken by the trojanized program in order to allow attackers to gain complete remote access. The installer is pulling a remote payload, which is encrypted to avoid detection. The malware can be used to target both Windows and MacOS users, which infers that significant resources were dedicated to carrying out this attack. The complexity and magnitude of this attack can indicate that it was state-sponsored. -
The distributed malware is complex and supports different operating systems.
Once installed, several steps are taken by the trojanized program in order to allow attackers to gain complete remote access. The installer is pulling a remote payload, which is encrypted to avoid detection. The malware can be used to target both Windows and MacOS users, which infers that significant resources were dedicated to carrying out this attack. The complexity and magnitude of this attack can indicate that it was state-sponsored. -
The attackers used dll side-loading exploitation technique
The following section refers to the Windows version of the attack but points out the approaches attackers have used to pull out this attack.
As can be seen in the technical analysis done by Sophos, the attackers have injected two different libraries into the MSI file: ffmpeg.dll and d3dcompiler_47.dll. ffmpeg is a famous open-source project to process audio files and more. While ffmpeg.dll is normally used by the 3CX Desktop App, the tempered version still retains every original functionality the original ffmpeg module had but also acts as a loader to the second malicious library d3dcompiler_47.dll.
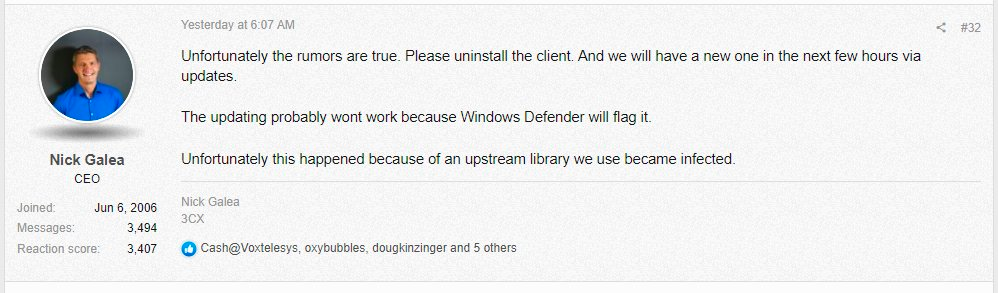
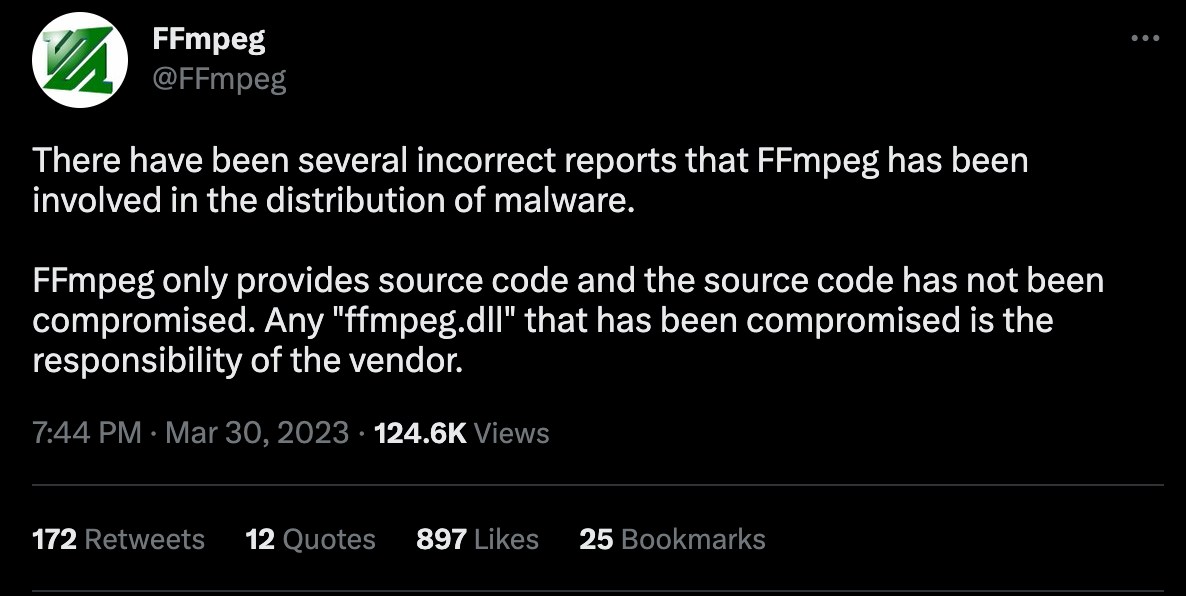
Nick Galea, 3CX’s CEO, has blamed ffmpeg for being compromised. But the ffmpeg Twitter account denies these accusations.
The ffmpeg library could have been tempered in several ways:-
The attackers were involved in the in-house ffmpeg build process. During the build process, the attackers were able to change the library’s functionality and link it to call d3dcompiler_47.dll
-
The attackers compromised 3CX’s package manager and replaced the legitimate module with the malicious one.
-
Another speculation is that 3CX holds an internal repository for ffmpeg source code which could also be tempered.
-
How To Prevent Your CI/CD Pipelines From Being Compromised
Software companies and organizations can pay a heavy price for letting their guard down on their software supply chain security. That’s why it’s essential to follow extra security measures to stay protected and keep your organization’s supply chain safe and sound. There are several steps you can take now to upgrade your CI/CD pipeline’s security:
-
Keep your secrets and passwords safe. Many times attacks such as this originate from leaked credentials, e.g., a developer mistakenly exposing an access token to their build server in a public code repository or through a widely accessible docker container. Always make sure your software assets don’t expose secrets to your CI/CD services. Employ guardrails throughout your development pipeline to provide continuous assurance.
-
Keep your SDLC assets, such as source code management system, build servers, and artifact registries, monitored and updated at all times. You need complete visibility over your pipeline to ensure you know the current versions and that these versions aren’t exposed to any known attacks. This includes updating plugins or revoking parts of your pipeline that are not maintained.
-
Make sure developers' privileges are limited. Separating dev and prod environments, preventing access to secrets, and adhering to the principle of least privilege can assure that your organization will suffer minimal impact if one of your developer's accounts gets compromised.
-
Employ secure development practices. Enforce policies and branch protection rules, such as mandatory code review, to keep the first parts of your software supply chain safe.
Legit Security Prevents Software Supply Chain Attacks
The Legit Security platform automatically inventories your end-to-end preproduction development environments and the relationship between systems. This encompasses source code management systems, build servers, and artifact registries – all the way through production deployment. Our SaaS platform alerts you in real-time when hundreds of security policies are violated in your software supply chain so that security teams can remediate critical security issues before they make it into production.
To learn more, schedule a product demo and check out the Legit Security Platform.
-1.jpg)