Get details on Legit's research on the security of custom GitHub Actions.
We recently published a report, called The State of GitHub Actions Security, which analyzes the security posture of GitHub Actions workflows and custom GitHub Actions. This report is based on an analysis of 2,500,000 GitHub Actions workflow files belonging to 553,000 organizations and personal users.
Some notable findings include the vulnerabilities lurking in custom GitHub Actions (those developed by the community to enhance GitHub Actions capabilities).
Most of the Actions there are not verified, maintained by one developer, and have low security scores based on OpenSSF Scorecard.
Verified Actions
Our research reveals that, of the 19,113 custom GitHub Actions in the marketplace, only 913 were created by verified GitHub users.
Verified Actions are Actions whose creator is verified by GitHub. Verification is a signal that the creator is credible, and Legit recommends using Actions from verified sources whenever possible.
Security Scorecard for Custom Actions
Legit used the scorecard project from OSSF to assess the security posture of each marketplace Action.
Among the entire sample, the scorecard score was 4.23 out of 10, highlighting the insecurity of custom GitHub Actions.
In addition, the graph below clearly illustrates that popular custom Actions exhibit consistently higher security scores on average, providing users with an additional compelling reason to opt for well-known and widely used custom Actions.

Unhandled Vulnerable Dependencies
Custom Actions with unhandled vulnerable dependencies are more likely to contain security issues and bugs. It also reflects on the Action author’s willingness to resolve security issues.
To determine if an Action has a vulnerable dependency, the Legit research team checked whether the repository contains Dependabot pull requests. Dependabot is an SCA scanner built into the GitHub platform that automatically creates fixing pull requests for vulnerable dependencies. For each Action, Legit counted the number of open Dependabot pull requests, as shown below.
| Open Dependabot Pull Requests | Number of Actions |
| > 20 | 24 |
| 1 - 10 | 3,139 |
| 10-20 | 366 |
Owner Account Age
Account age highlights the author’s experience, expertise, and dedication to the platform. Indicating a track record of contributions and engagement within the open-source community, account age can establish trust among users.
Legit research found that most custom Actions are written by developers with less than
one year of experience.

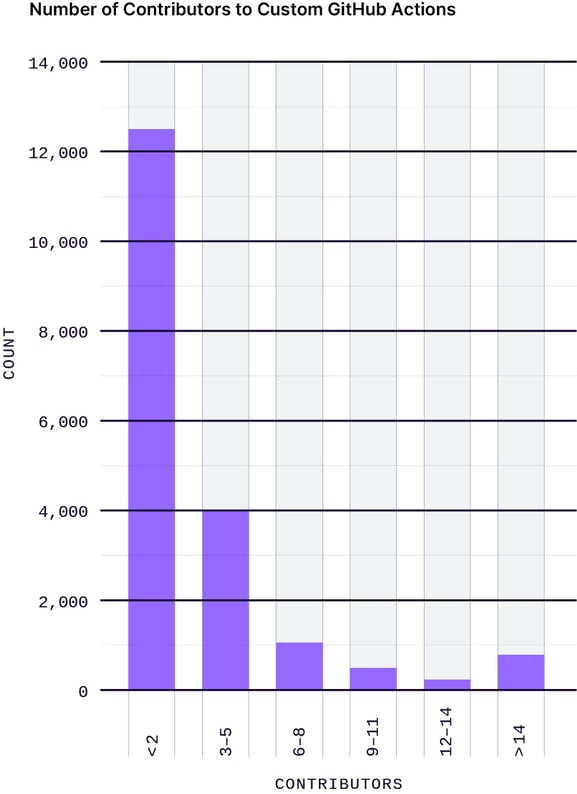
Contributors
The number of contributors to a custom Action strongly reflects its credibility. A higher number of contributors indicates broader community involvement and active development. This collaborative effort leads to increased security, testing, and overall quality.
Unfortunately, most of the GitHub Actions in the marketplace are maintained by a single developer. This could be the case because many custom Actions have small scopes and don’t require a lot of effort to create and maintain.
Archived
We found 762 archived marketplace Actions.
Using archived Actions presents a couple of problems. First, archived Actions do
not receive regular updates or bug fixes, potentially leading to compatibility issues or security vulnerabilities. Second, the lack of ongoing maintenance and support for archived Actions makes it challenging to address any issues raised by GitHub users.
Recommendations on Custom GitHub Actions Use
Custom Actions, although useful, pose a significant risk for workflow authors. To limit the risk, adhere to strict standards when using them. Make sure that you import Actions from verified owners, and those that are active, maintained, and have high security scores.
In addition to only using custom Actions after thoroughly vetting them, organizations should use GitHub’s built-in features to enforce GitHub Actions best practices and policies, including:
- Creating a list of allowed third-party Actions
- Configuring default permission for workflow tokens to be
- the least privileged
- Determining where GitHub Actions can approve pull requests
- Controlling which users can execute workflows
For more data and recommendations on GitHub Actions security, see our new research report, The State of GitHub Actions Security.
Download our new whitepaper.


