Jenkins is an open-source automation and build platform that allows for automated tests, integrations, builds, and much more. However, Jenkins also has vulnerabilities that make it susceptible to software supply chain attacks. See how attackers used compromised Jenkins plugins to launch cyberattacks and how to detect vulnerable Jenkins plugins at scale.
Part 1: The Threat
Almost every software pipeline has an integrated build system to enable CI/CD. There are many popular build platforms, and most platforms provide an initial set of tools that can be extended using a marketplace of 3rd party plugins, modules, and libraries.
In this blog, we are going to walk through what Jenkins plugins are, how they are used, and why it’s critical to detect vulnerable Jenkins plugins. We will also elaborate on what a good solution to this problem looks like to help protect your organization from this emerging risk.
About Jenkins
Jenkins is an open-source automation and build platform. It allows automating tests, integrations, issues, builds, and much more. Jenkins is typically run as a standalone application in its own process with the built-in Java servlet container/application server. Many organizations that use Jenkins have their own infrastructure to run the application and agents. This also means that each organization is responsible for managing and monitoring Jenkins resources, and importantly - security.
Jenkins plugins
Plugins were introduced to extend Jenkins functionality. Currently, there are over 1,800 open-source plugins being used by the community. Some plugins are dedicated to integrating with external services, and some are made to improve testing and building. Popular plugins have almost 300,000 downloads meaning each plugin can have an impact on millions of projects. In the image below, you can see the most popular plugins sorted by installs (Search Results). You can also see that there are plugins for many usages, such as storing SSH credentials, API enabling, testing, and many others.
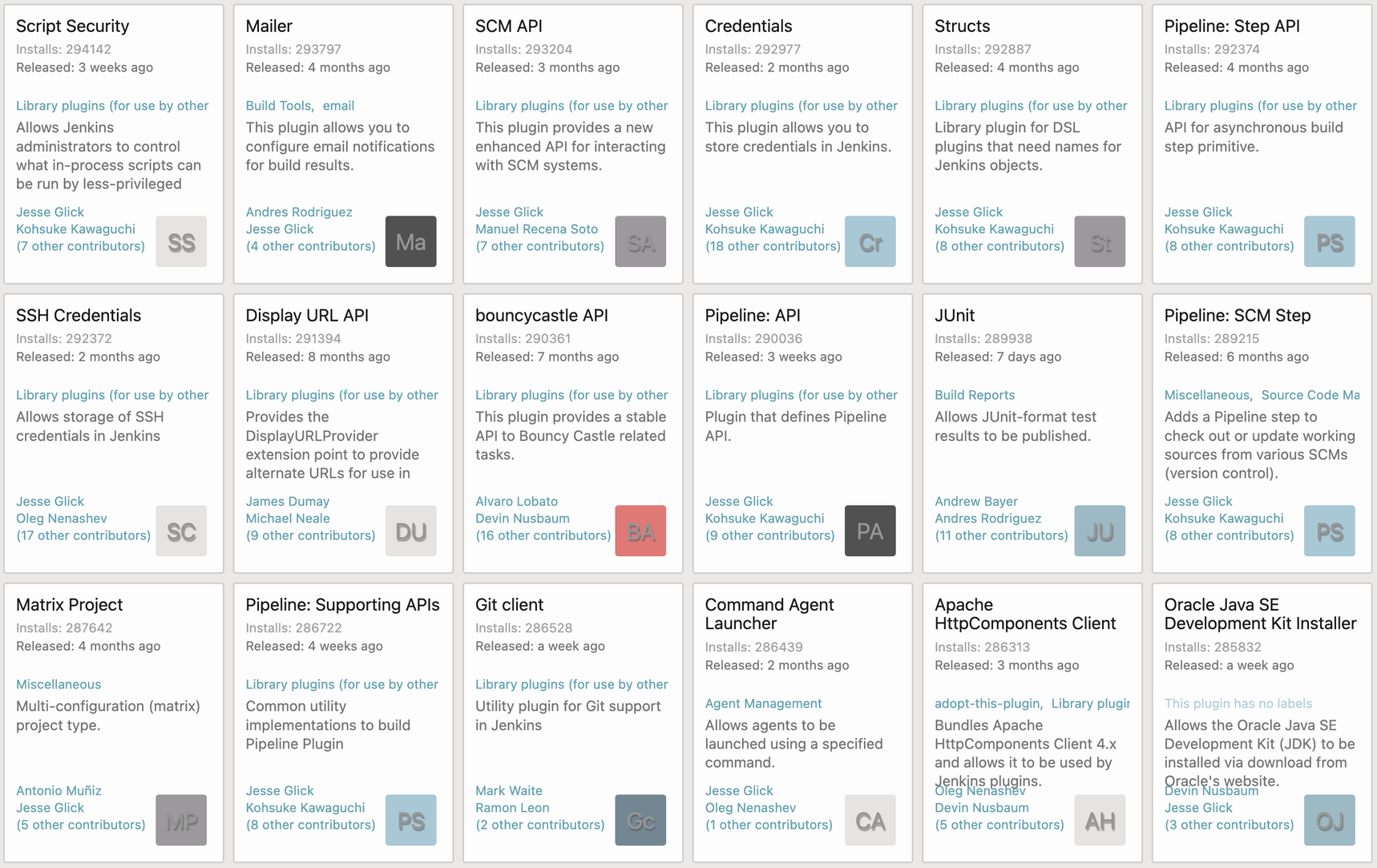
An ocean of plugins available to add functionality to your development life cycle
Vulnerable Jenkins Plugins
Jenkins plugins can have powerful permissions, such as:
- GitHub permissions include merging pull requests, pushing to repositories, managing GitHub applications, etc.
- Release Permissions to deploy releases to the Jenkins artifact repository. Snapshots can be deployed by contributors without this permission.
- Plugins can also have the ability to create a network connection and expose another endpoint to your Jenkins environment.
The combination of a plugin's permissions, network access, and code access makes Jenkins plugins a sweet spot for attackers looking for an easy way to infiltrate your software supply chain.
“We strive to fix all security vulnerabilities in Jenkins and plugins in a timely manner. However, the structure of the Jenkins project, which gives plugin maintainers a lot of autonomy, and the number and diversity of plugins make this impossible to guarantee.” - Handling Vulnerabilities in Plugins
There could be many different types of vulnerabilities detected in plugins; for example, in the advisory from October 2022 - Jenkins Security Advisory 2022-10-19, 28 different plugins were found vulnerable to different vulnerability types such as XSS, CSRF, Sandbox bypass, and more. All of these vulnerabilities might lead to remote code execution, data leak, and lateral movement.
As mentioned before, the Jenkins platform is usually self-managed, which means that plugin security should also be a top concern of an organization’s Security and DevSecOps Teams. Many organizations use Jenkins inside an internal network which makes automated monitoring for vulnerable plugins more difficult.
CVE-2022-34777 - A GitLab Plugin case study
To demonstrate the impact of a vulnerable plugin, we will explain and analyze CVE-2022-34777 - a stored XSS vulnerability published on 06/30/2022.
We have installed the vulnerable version to show how this vulnerability can be easily exploited. In our case, the Jenkins server was connected to the Internet, and the Jenkins engine alerted us of a vulnerable plugin version. A Jenkins server that is used inside an internal network will not show this warning.
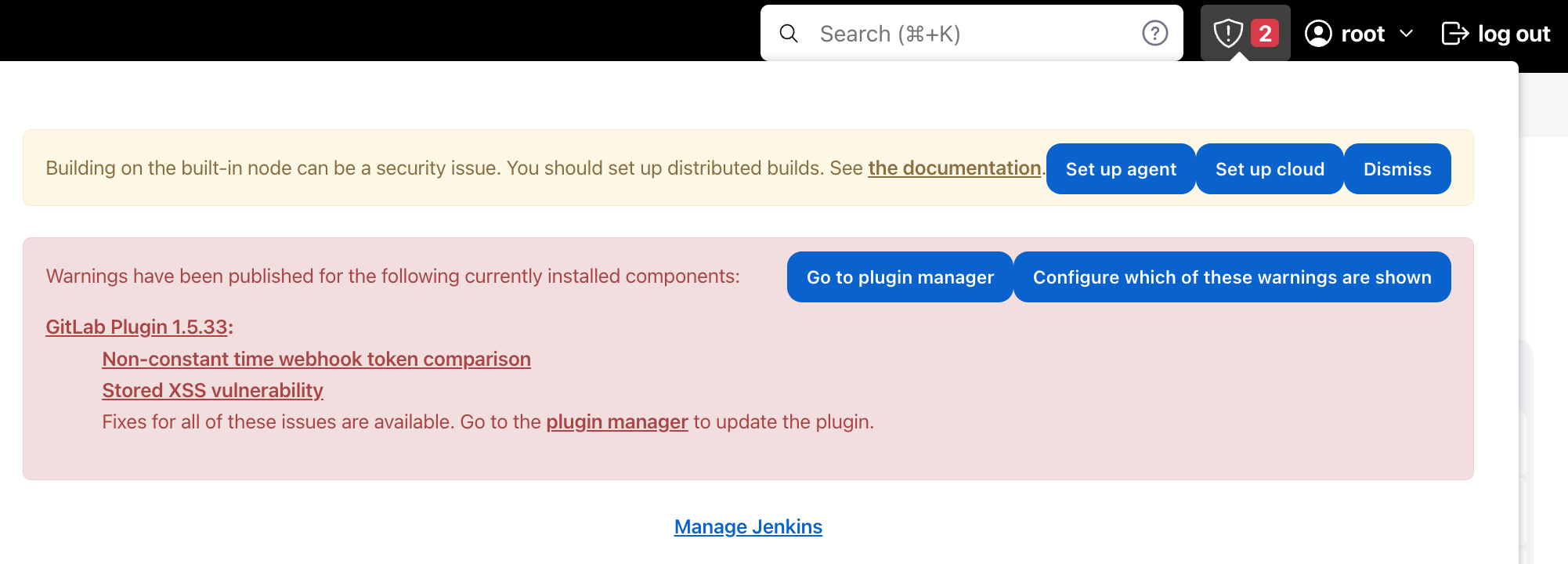
A warning message for the vulnerable plugin
The GitLab plugin allows GitLab to trigger builds in Jenkins when code is committed or merge requests are opened/updated. It can also send the build status back to GitLab.
The vulnerability allowed attackers with issue permissions to trigger a carefully crafted webhook that resulted in a victim browsing a Jenkins pipeline being attacked with a malicious JavaScript payload.
CVE-2022-34777 Exploitation POC
In the example video, you can see how a repository with a merge request triggers a webhook. Initially, we demonstrate how a normal push event triggers a pipeline run but then, we show how we created a merge- request that will end up in remote malicious JavaScript code being executed in Jenkins.
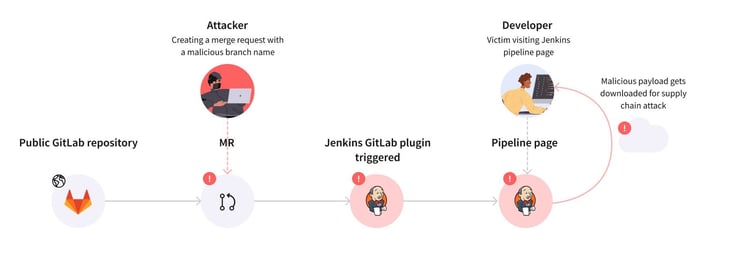
CVE-2022-34777 Attack Vector
The impact of an attack described in the image above could be devastating for an organization. An attacker could potentially gain sensitive information such as access tokens or private code.
Part 2: How to Solve The Problem
How to Detect Vulnerable Jenkins Plugins at Scale
Continuously monitoring the CVEs and cross-referencing them with all the plugins that are currently active in your Jenkins servers can be extremely time-consuming. Depending on your size, this problem is beyond human scale. Even for smaller organizations, using automated technology to do this task can be a better use of already-scarce security resources. At Legit Security, we have created a capability whereby, after integrating with us, we scan your server, create an inventory of all of the plugins and continuously alert you should any of them be vulnerable. Legit provides you with an instantaneous alert as soon as the CVE is published, so you can protect your organization before cyber criminals try to usurp the vulnerability. This is especially effective for zero-day vulnerabilities where time is extremely critical.
Additionally, we provide you with critical information on the vulnerability and where it affects you so that you have all the pieces of the puzzle and can remediate them in a timely manner. In order to help you with the remediation, Legit helps you prioritize security issues throughout your remediation process by surfacing the most critical vulnerabilities first, giving you the context to know whether a vulnerable plugin has the ability to affect the SDLC of business-critical applications, for example.
Once the issue has been found, users can choose their preferred method or process for remediation. You can create custom automations that take actions such as automated ticket creation and assignment to the relevant parties and stakeholders. Finally, Legit provides you with a step-by-step guide on how to fix the security issues that were found.
It Takes Minutes to Assess Your Risk of Vulnerable Jenkins Plugins With Legit
In addition to continuously identifying your vulnerable Jenkins plugins, Legit continuously monitors and auto-discovers “shadow build infrastructure”. This ensures that the inventory and Jenkins servers you need to protect is not hiding from your view. Without an accurate inventory of the Jenkins servers used in your SDLC, you cannot assess your risk to vulnerable Jenkins plugins.
Legit also helps with a wide range of other software supply chain security challenges to protect you from software supply chain attacks. Learn more about Legit by visiting our platform page or booking a demo with us today.
-1.jpg)